

Employee Security & Training
Secures and trains employees whilst monitoring the threats they face
How do I protect my organisation from cybersecurity threats designed to target my staff?
One of the most important things you can do to protect your organisation is to ensure that your staff are aware of the potential dangers of being targeted by cybercriminals. You can do this by assessing your technology and providing cybersecurity awareness training.
This will help to identify and avoid cyber threats, stay up to date on the latest trends, and have a clear, well-communicated cybersecurity policy.
Risks and concerns you face without cybersecurity training for staff
Cybersecurity training for staff is crucial to avoid risks and pressures on your organisation. Without the proper employee security training, your organisation can open its doors to cyber attacks.
With a remote workforce becoming increasingly popular, it is important that cybersecurity awareness training is conducted to reduce the risk of your employees unwittingly becoming a potential cybersecurity threat.
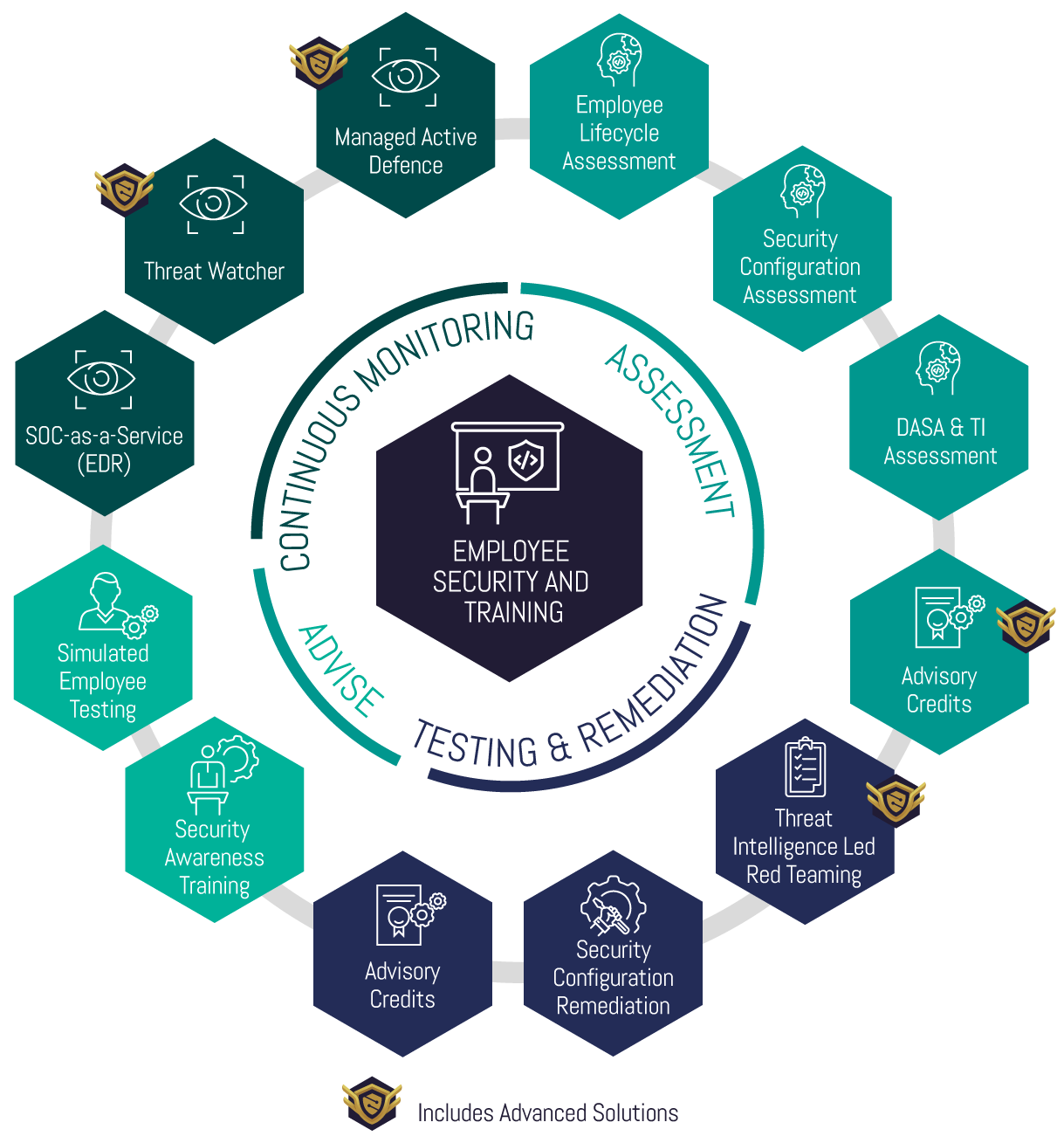
Package Approach
This package has four core phases and is a guided programme focused on technology and employees.
Assessment
• The programme commences with detailed assessment activity aimed at understanding the technology and security posture of your employees.
Testing and Remediation
• Provides detailed objective-based testing. This is followed by remediation and rectification of security and technology configuration ensuring a robust posture is built.
Advise
• Delivers end-user awareness training programs combined with technology-based simulation tests to ensure a continually improving approach to maturity.
Continuous Monitoring
• Provision of services that support detection, protection, and response capability to cyber threats targeting your employees.
Choose our Employee Security & Training package
This package ensures that your technology is secure, trains your employees effectively, and deploys services to ensure continual monitoring of threats.
The package is split into two offerings, Baseline and Advanced, select your package below.


Baseline Package
• Technical Account Manager (TAM)
A Technical Account Manager (TAM) is your first line of engagement and ensures you are led through the delivery of work streams required.
The TAM works with your team to drive priorities, deliver value, and align with your business concerns, risks, and drivers. Pivoting between LRQA Nettitude’s operational teams and your staff they liaise regularly, helping to schedule work, and ensure delivery.
• Advisory Credits
• Employee Lifecycle Assessment
• Security Configuration Assessment
• Security Awareness Training
• Simulated Employee Testing
LRQA Nettitude aims to engage your people with phishing emails, and we will test and evaluate your employees’ security awareness and vulnerability level.
• Digital Attacks Surface Assessment
• Threat Intelligence Key Persons Assessment
• Data Loss Prevention Solutions
Helps your organisation detect and prevent data breaches. Typically, this focuses attention on the environment perimeter, in the form of email or web access and endpoint control.
• Managed Detection and Response
In today’s world, endpoint protection is becoming a necessity to be able to reduce the likelihood of an adversary attacking your organisation, leading to a data breach, Ransomware, or other malicious action against you.
Endpoint Detection and Response (EDR) solutions are configured to be able to defend and alert against these malicious activities, helping to reduce the time to detect and respond to an incident.
• Threat Intelligence Services
LRQA Nettitude’s ThreatWatcher service provides a managed assessment using advanced reconnaissance and analytics to identify previously unknown threats that could be used against your organisation in a cyberattack.
Security intelligence from ThreatWatcher can highlight weaknesses in your user education and help to identify your digital attack surface like never before. Once understood the recommendations from the assessment can supercharge risk reduction across your organisation and help drive your organisation to an intelligence-led security strategy.
Advanced Package
• Technical Account Manager (TAM)
A Technical Account Manager (TAM) is your first line of engagement and ensures you are led through the delivery of work streams required.
The TAM works with your team to drive priorities, deliver value, and align with your business concerns, risks, and drivers. Pivoting between LRQA Nettitude’s operational teams and your staff they liaise regularly, helping to schedule work, and ensure delivery.
• Advisory Credits
• Employee Lifecycle Assessment
• Security Configuration Assessment
• Security Awareness Training
Reduces your cyber risk by improving your employees’ cybersecurity knowledge, or their understanding of how to deal with digital data in general. We will train your employees on identifying threats and teach the ways to protect themselves from those threats.
• Simulated Employee Testing
LRQA Nettitude aims to engage your people with phishing emails, and we will test and evaluate your employees’ security awareness and vulnerability level.
• Digital Attacks Surface Assessment
Digital Attack Surface Assessment was created in order to provide organisations with a detailed overview of their digital footprint which includes areas such as credential exposures, similar domain name assessment, is the company being mentioned on the dark web or in deep web forums, the risk from third parties, and shadow infrastructure associated to them.
• Threat Intelligence Key Persons Assessment
• Data Loss Prevention Solutions
Helps your organisation detect and prevent data breaches. Typically, this focuses attention on the environment perimeter, in the form of email or web access and endpoint control.
• Managed Detection and Response
In today’s world, a SIEM solution combined with endpoint protection is becoming a necessity to be able to reduce the likelihood of an adversary attacking your organisation, leading to a data breach, Ransomware, or other malicious action against you.
SIEM and Endpoint Detection and Response (EDR) solutions are configured to be able to defend and alert against these malicious activities, helping to reduce the time to detect and respond to an incident.
• Advanced Threat Intelligence Services
LRQA Nettitude’s ThreatWatcher service provides a managed assessment using advanced reconnaissance and analytics to identify previously unknown threats that could be used against your organisation in a cyberattack.
Security intelligence from ThreatWatcher can highlight weaknesses in your user education and help to identify your digital attack surface like never before. Once understood the recommendations from the assessment can supercharge risk reduction across your organisation and help drive your organisation to an intelligence-led security strategy.
• Red Teaming
We simulate threat attack paths to your assets (not just compromising your perimeter). This tooling allows the Red Team to simulate real-world threats against your organisation in the closest manner to a real attack.
A Red team creates in-depth attack paths that mimic a wide range of sophisticated scenarios and inform you clearly of the current assurance levels around a cyber-attack.
• Managed Vulnerability Scanning
Deploys a leading cloud-based vulnerability scanning and management technology to identify, investigate, prioritise, mitigate, and respond to vulnerabilities within your environment.
Failing to understand and remediate the vulnerabilities within your environment could present an attacker with the opportunity they need to gain access to your systems.
• Managed Threat Hunting
The world of technology moves at a rapid pace and as such there are new techniques used by attackers to compromise organisations which may evade traditional detection solutions.
Our Threat Hunt-as-a-Service is provided using a mixture of sophisticated technology and highly certified threat hunters to provide assurance and identify whether your organisation is currently compromised, or even where historic compromise activity has occurred.
It understands the impact of any discovered breach and provides actionable guidance on the next steps to respond to and eradicate the threat.
Get in touch…
Explore More Cyber Packages…
Ransomware & Malware
How safe is your organization from a ransomware threat? Ensure you are always prepared for a ransomware or malware attack with this package.
Learn More…
Cyber Breach Readiness
Is your organization prepared for a cyber breach? This package prepares your organization and ensures you can respond to a breach.
Learn More…
Supplier & Third-Party Risk Management
Can you trust your supplier’s and third-parties cybersecurity? Select this package for complete assurance, governance, and risk management of your supply chain.
Learn More…
Penetration Testing Remediation
Penetration Tests have identified your weaknesses, but do you know how to remediate vulnerabilities? Select this package to ensure remediation is fully executed.
Learn More…
New Technology Cyber Risks
Concerned that moving to new technology will increase cyber risks? Choose this package for assurance that new technology is secured and protected by experts.
Learn More…
Technical Legacy Debt
Do you know legacy software systems can expose you to cyber threats? Ensure your systems are safe with this package to manage and secure legacy systems.
Learn More…


Employee Security & Training
Secures and trains employees whilst monitoring the threats they face
How do I protect my organisation from cybersecurity threats designed to target my staff?
One of the most important things you can do to protect your organisation is to ensure that your staff are aware of the potential dangers of being targeted by cybercriminals.
You can do this by providing cyber security awareness training on identifying and avoiding cyber threats, staying up to date on the latest trends, and having a clear, well-communicated cybersecurity policy.
Risks and concerns you face without cybersecurity training for staff
Cybersecurity training for staff is crucial to avoid the following associated risks and pressures on your organisation. Without the proper employee security training in place, your organisation can open its doors to cyber attacks.
With a remote workforce becoming increasingly popular within organisations, it is ever important that cybersecurity awareness training for employees is conducted; training your staff in best practice, thus reducing the risk of your employees unwittingly becoming a potential cybersecurity threat.
Package Approach
This package has four core phases and is a guided programme focused on technology and employees.
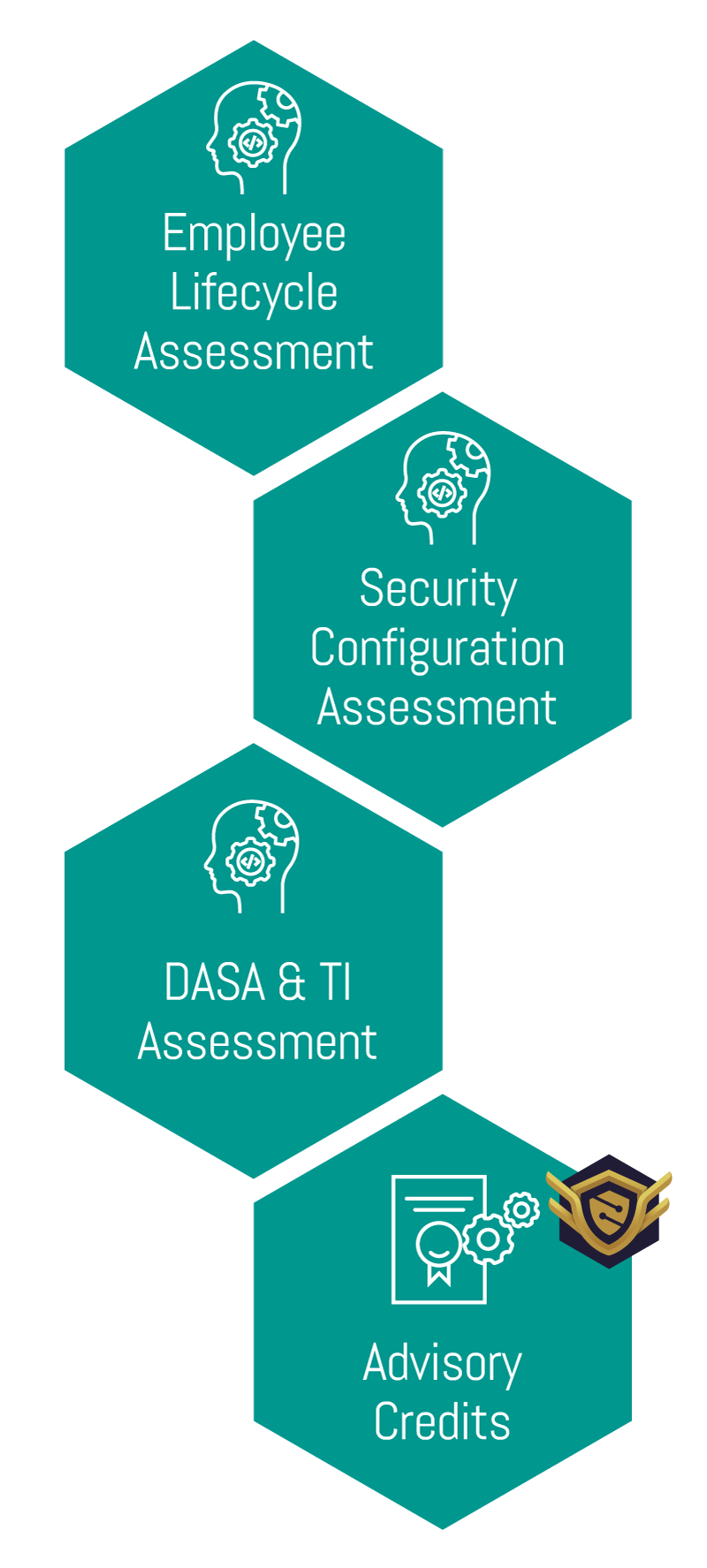
Assessment
The programme commences with detailed assessment activity aimed at understanding the technology and security posture of your employees.
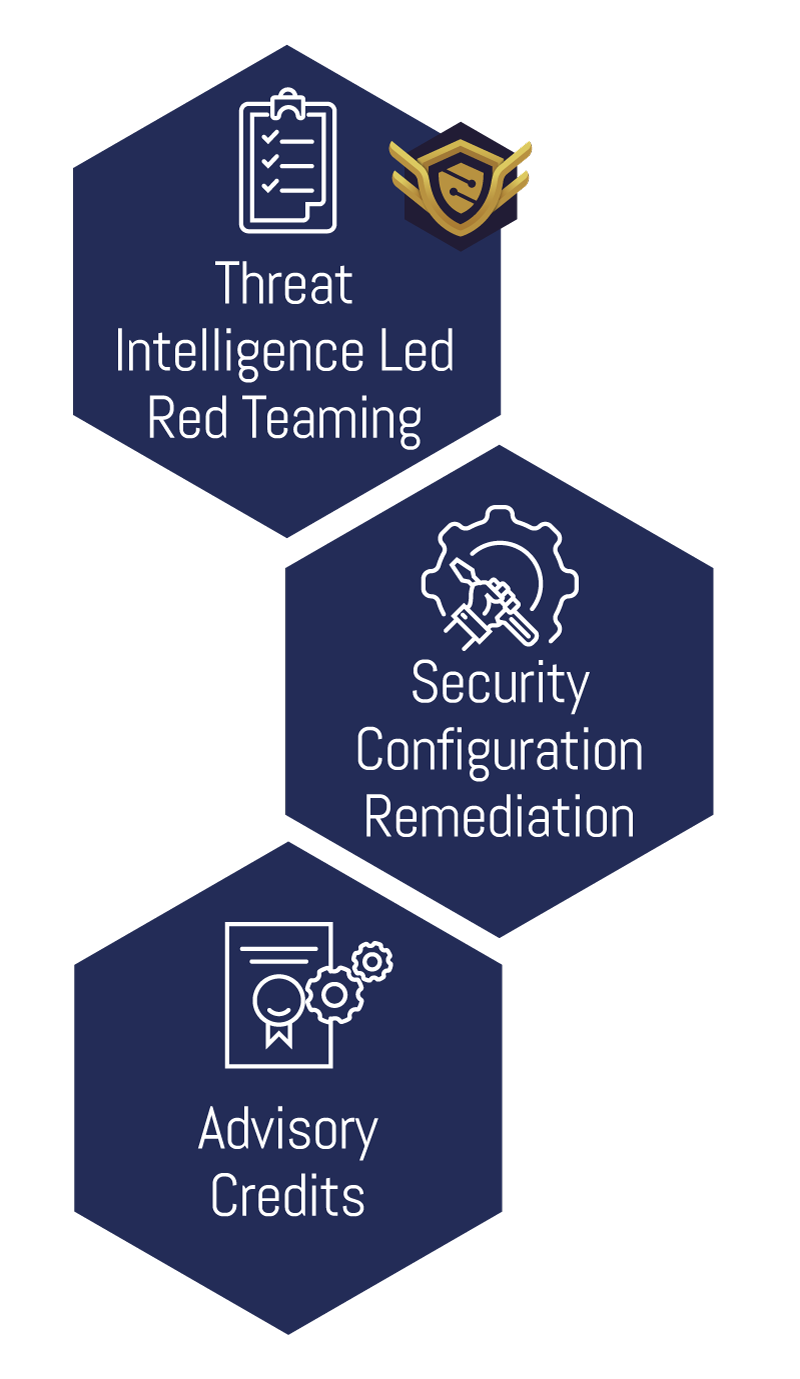
Testing and Remediation
Provides detailed objective-based testing. This is followed by remediation and rectification of security and technology configuration ensuring a robust posture is built.
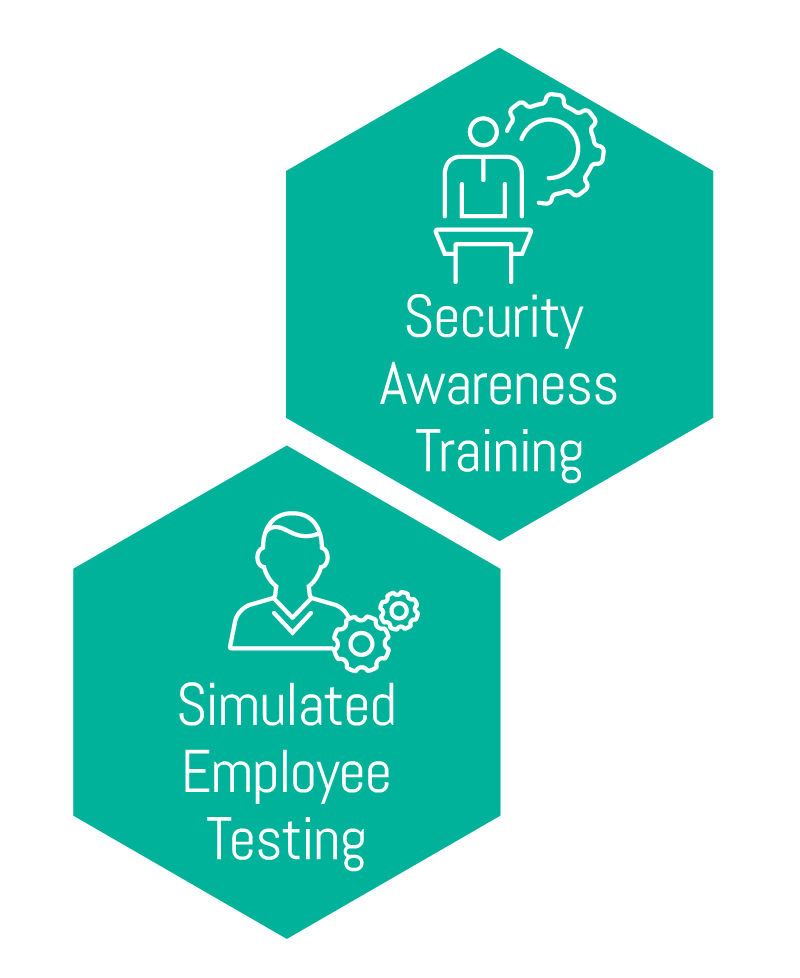
Advise
Delivers end-user awareness training programs combined with technology-based simulation tests to ensure a continually improving approach to maturity.
Continuous Monitoring
Provision of services that support detection, protection, and response capability to cyber threats targeting your employees.
Choose our Employee Cyber Training package
This package ensures that your technology is secure, trains your employees effectively, and deploys services to ensure continual monitoring of threats.
The package is split into two offerings, Baseline and Advanced, select your package below.

Baseline Package
• Technical Account Manager (TAM)
A Technical Account Manager (TAM) is your first line of engagement and ensures you are led through the delivery of work streams required.
The TAM works with your team to drive priorities, deliver value, and align with your business concerns, risks, and drivers. Pivoting between LRQA Nettitude’s operational teams and your staff they liaise regularly, helping to schedule work, and ensure delivery.
• Advisory Credits
• Employee Lifecycle Assessment
• Security Configuration Assessment
• Security Awareness Training
Reduces your cyber risk by improving your employees’ cybersecurity knowledge, or their understanding of how to deal with digital data in general. We will train your employees on identifying threats and teach the ways to protect themselves from those threats.
• Simulated Employee Testing
LRQA Nettitude aims to engage your people with phishing emails, and we will test and evaluate your employees’ security awareness and vulnerability level.
• Digital Attacks Surface Assessment
Digital Attack Surface Assessment was created in order to provide organisations with a detailed overview of their digital footprint which includes areas such as credential exposures, similar domain name assessment, is the company being mentioned on the dark web or in deep web forums, the risk from third parties, and shadow infrastructure associated to them.
• Threat Intelligence Key Persons Assessment
• Data Loss Prevention Solutions
Helps your organisation detect and prevent data breaches. Typically, this focuses attention on the environment perimeter, in the form of email or web access and endpoint control.
• Managed Detection and Response
In today’s world, endpoint protection is becoming a necessity to be able to reduce the likelihood of an adversary attacking your organisation, leading to a data breach, Ransomware, or other malicious action against you.
Endpoint Detection and Response (EDR) solutions are configured to be able to defend and alert against these malicious activities, helping to reduce the time to detect and respond to an incident.
• Threat Intelligence Services
LRQA Nettitude’s ThreatWatcher service provides a managed assessment using advanced reconnaissance and analytics to identify previously unknown threats that could be used against your organisation in a cyberattack.
Security intelligence from ThreatWatcher can highlight weaknesses in your user education and help to identify your digital attack surface like never before. Once understood the recommendations from the assessment can supercharge risk reduction across your organisation and help drive your organisation to an intelligence-led security strategy.

Advanced Package
• Technical Account Manager (TAM)
A Technical Account Manager (TAM) is your first line of engagement and ensures you are led through the delivery of work streams required.
The TAM works with your team to drive priorities, deliver value, and align with your business concerns, risks, and drivers. Pivoting between LRQA Nettitude’s operational teams and your staff they liaise regularly, helping to schedule work, and ensure delivery.
• Advisory Credits
• Employee Lifecycle Assessment
• Security Configuration Assessment
• Security Awareness Training
Reduces your cyber risk by improving your employees’ cybersecurity knowledge, or their understanding of how to deal with digital data in general. We will train your employees on identifying threats and teach the ways to protect themselves from those threats.
• Simulated Employee Testing
LRQA Nettitude aims to engage your people with phishing emails, and we will test and evaluate your employees’ security awareness and vulnerability level.
• Digital Attacks Surface Assessment
Digital Attack Surface Assessment was created in order to provide organisations with a detailed overview of their digital footprint which includes areas such as credential exposures, similar domain name assessment, is the company being mentioned on the dark web or in deep web forums, the risk from third parties, and shadow infrastructure associated to them.
• Threat Intelligence Key Persons Assessment
• Data Loss Prevention Solutions
Helps your organisation detect and prevent data breaches. Typically, this focuses attention on the environment perimeter, in the form of email or web access and endpoint control.
• Managed Detection and Response
In today’s world, a SIEM solution combined with endpoint protection is becoming a necessity to be able to reduce the likelihood of an adversary attacking your organisation, leading to a data breach, Ransomware, or other malicious action against you.
SIEM and Endpoint Detection and Response (EDR) solutions are configured to be able to defend and alert against these malicious activities, helping to reduce the time to detect and respond to an incident.
• Advanced Threat Intelligence Services
LRQA Nettitude’s ThreatWatcher service provides a managed assessment using advanced reconnaissance and analytics to identify previously unknown threats that could be used against your organisation in a cyberattack.
Security intelligence from ThreatWatcher can highlight weaknesses in your user education and help to identify your digital attack surface like never before. Once understood the recommendations from the assessment can supercharge risk reduction across your organisation and help drive your organisation to an intelligence-led security strategy.
• Red Teaming
We simulate threat attack paths to your assets (not just compromising your perimeter). This tooling allows the Red Team to simulate real-world threats against your organisation in the closest manner to a real attack.
A Red team creates in-depth attack paths that mimic a wide range of sophisticated scenarios and inform you clearly of the current assurance levels around a cyber-attack.
• Managed Vulnerability Scanning
Deploys a leading cloud-based vulnerability scanning and management technology to identify, investigate, prioritise, mitigate, and respond to vulnerabilities within your environment.
Failing to understand and remediate the vulnerabilities within your environment could present an attacker with the opportunity they need to gain access to your systems.
• Managed Threat Hunting
The world of technology moves at a rapid pace and as such there are new techniques used by attackers to compromise organisations which may evade traditional detection solutions.
Our Threat Hunt-as-a-Service is provided using a mixture of sophisticated technology and highly certified threat hunters to provide assurance and identify whether your organisation is currently compromised, or even where historic compromise activity has occurred.
It understands the impact of any discovered breach and provides actionable guidance on the next steps to respond to and eradicate the threat.
Get in touch…
Explore More Cyber Packages…
Ransomware & Malware
How safe is your organization from a ransomware threat? Ensure you are always prepared for a ransomware or malware attack with this package.
Learn More…
Cyber Breach Readiness
Is your organization prepared for a cyber breach? This package prepares your organization and ensures you can respond to a breach.
Learn More…
Supplier & Third-Party Risk Management
Can you trust your supplier’s and third-parties cybersecurity? Select this package for complete assurance, governance, and risk management of your supply chain.
Learn More…
Employee Security & Training
Concerned about how to protect against threats that target employees? This package will secure and train employees while monitoring the threats they face.
Learn More…
Penetration Testing Remediation
Penetration Tests have identified your weaknesses, but do you know how to remediate vulnerabilities? Select this package to ensure remediation is fully executed.
Learn More…
New Technology Cyber Risks
Concerned that moving to new technology will increase cyber risks? Choose this package for assurance that new technology is secured and protected by experts.
Learn More…
Technical Legacy Debt
Do you know legacy software systems can expose you to cyber threats? Ensure your systems are safe with this package to manage and secure legacy systems.
Learn More…

Develop a Cybersecurity Programme
Can you prevent, withstand, and recover from cyber incidents? This package builds a cyber strategy equipping you against evolving threats.
Learn More…











