MANAGED ACTIVE DEFENCE
Proactive Defence to combat advanced Threats
The LRQA Nettitude Managed Active Defence service deploys a next-generation deception platform provided by Attivo Networks to provide an active defence to your security services.
LRQA Nettitude is an award-winning cybersecurity organisation with unparalleled capability in delivering managed security services. Through our global Security Operations Centres (SOCs) we deliver round the clock services that secure our clients and detect and respond to sophisticated cyber-threats, providing assurance that your organisation is protected.
What Is Managed Active Defence?
A shift from the defensive to an offensive security posture is necessary if organisations with sensitive and high-value data assets are to gain the upper hand in their battle against modern security threats. In assuming such a stance, organisations now look to deception and decoy systems for post-infection breach detection.
LRQA Nettitude Managed Active Defence is a next-generation solution using the Attitvo Networks platform. It provides advanced detection, protection, and SOAR use cases across a wide variety of network environments. The service is delivered 24/7 365, providing deception plans and orchestration playbooks all year round, tailored to your needs.
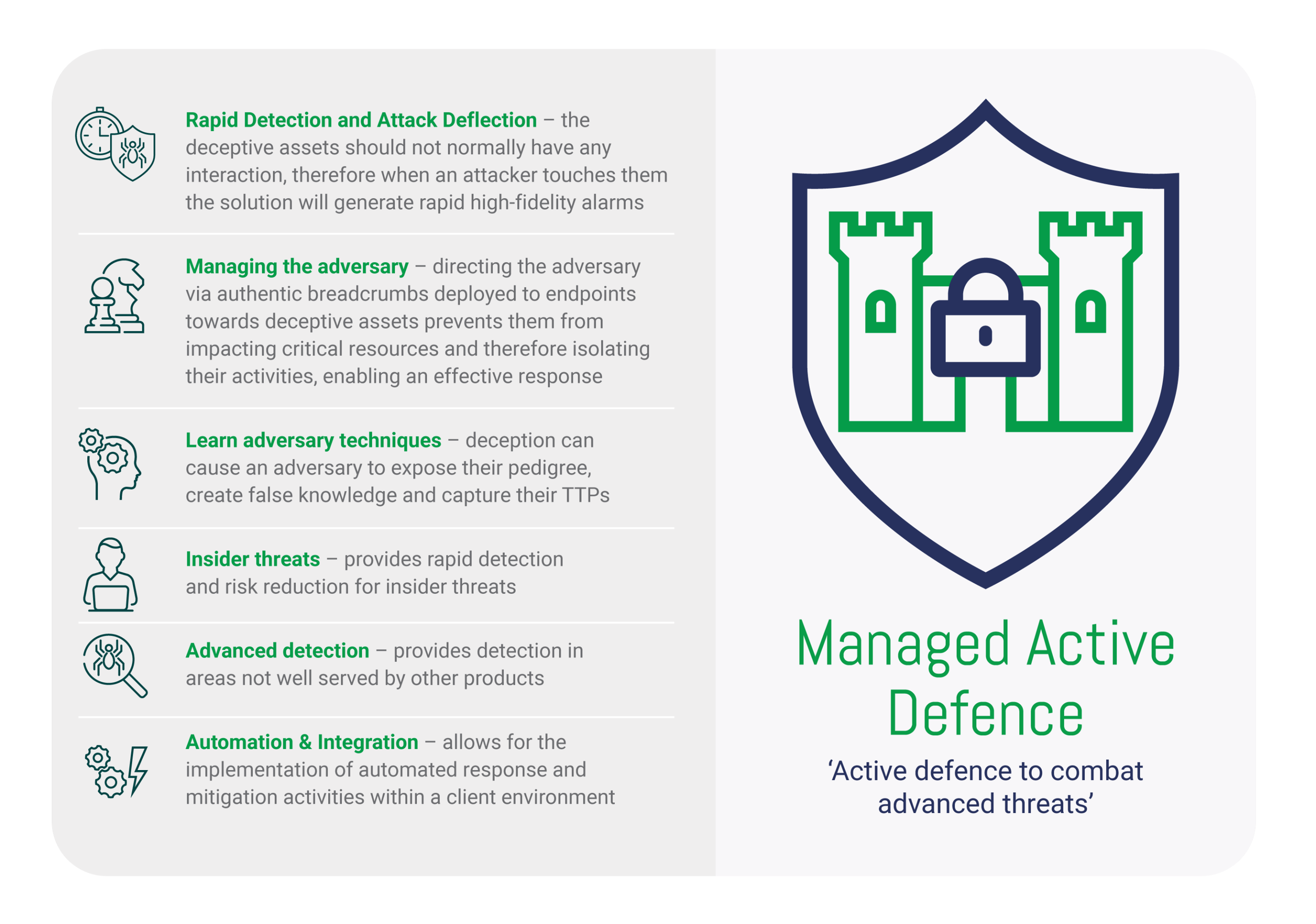
Deception platforms, such as our managed Attivo deception platform, are designed to detect and analyse all attack activity. This includes reconnaissance, lateral movement, stolen credential usage, malware and ransomware attacks, and man-in-the-middle activity.
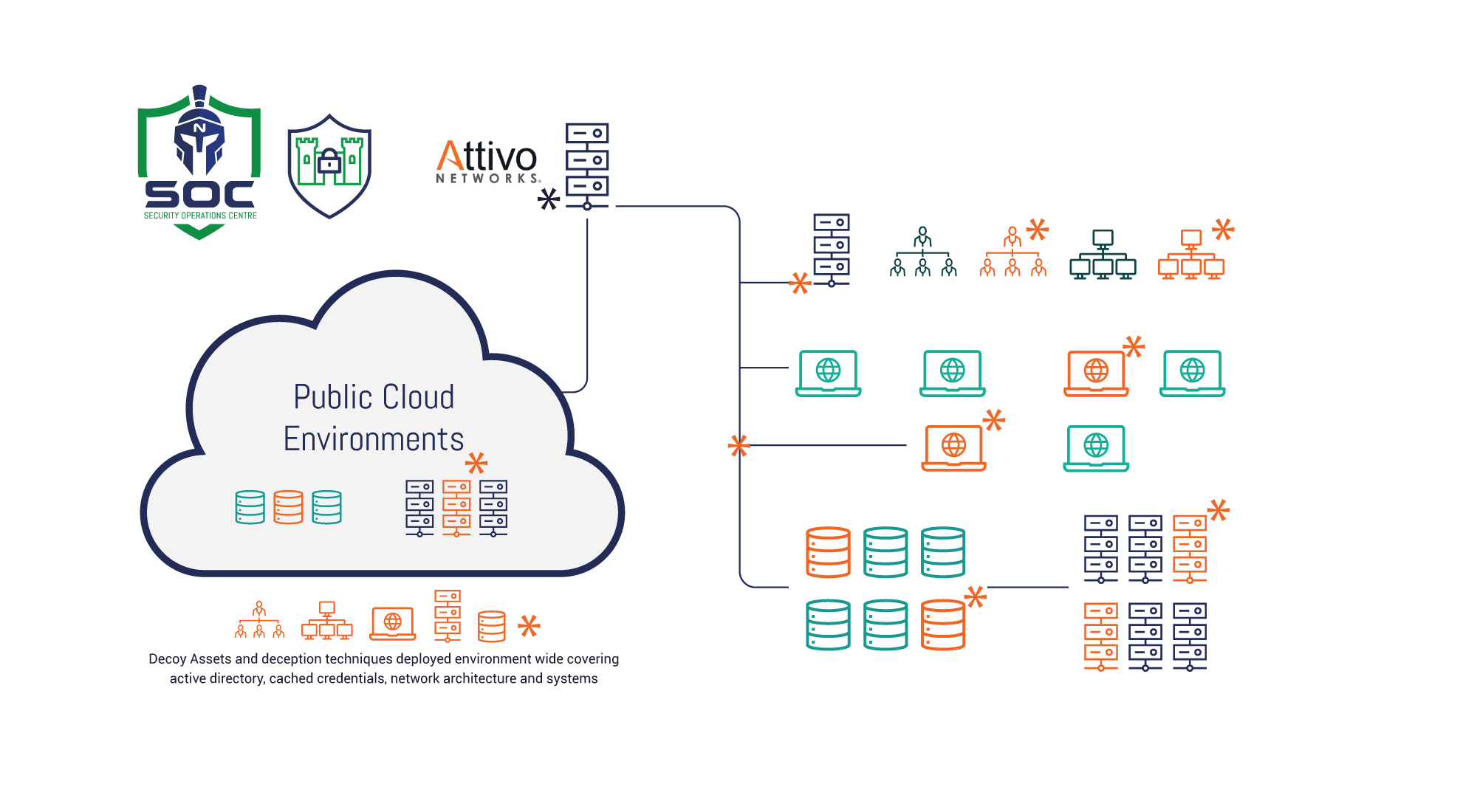
The Attivo Networks ThreatDefend® platform uses fully customisable virtual machines to mimic production assets. This ranges from Windows and Linux servers to IoT and SCADA devices and projects them throughout the network. The solution enables security organisations to lay tripwires throughout the network turning the entire IT environment into a trap. Deception allows you to turn the tables on attackers and force them to be 100% correct in their movements or risk detection by the security team.
“Judicious use of networks, pocket litter, and honeytokens can waste the adversary’s time and resources, expose their pedigree, and create false knowledge on their part. Deception can also add randomness and unpredictability to an architecture, network traffic, service, or mission activity, making an adversary’s understanding of the environment more challenging and at best inaccurate.” (Mitre, The Cyberspace advantage: Inviting them in)
About Attivo Networks
Attivo Networks® provide an innovative defence for protection against identity compromise, privilege escalation, and lateral movement attacks. The company’s solutions deliver unprecedented visibility, prevention, and derailment for security exposures, attack paths, and attack escalation activities across endpoints, Active Directory, and cloud environments.
Why Do You Need Managed Active Defence?
Attivo is a next-generation detection and prevention solution. It utilises deception techniques to fool an adversary into thinking they have control and access to the legitimate system and network resources.
The attacker is fed false information around Active Directory, cached credentials, connections to other systems, network architecture, and important assets and is led to interacting with fake hosts documents.
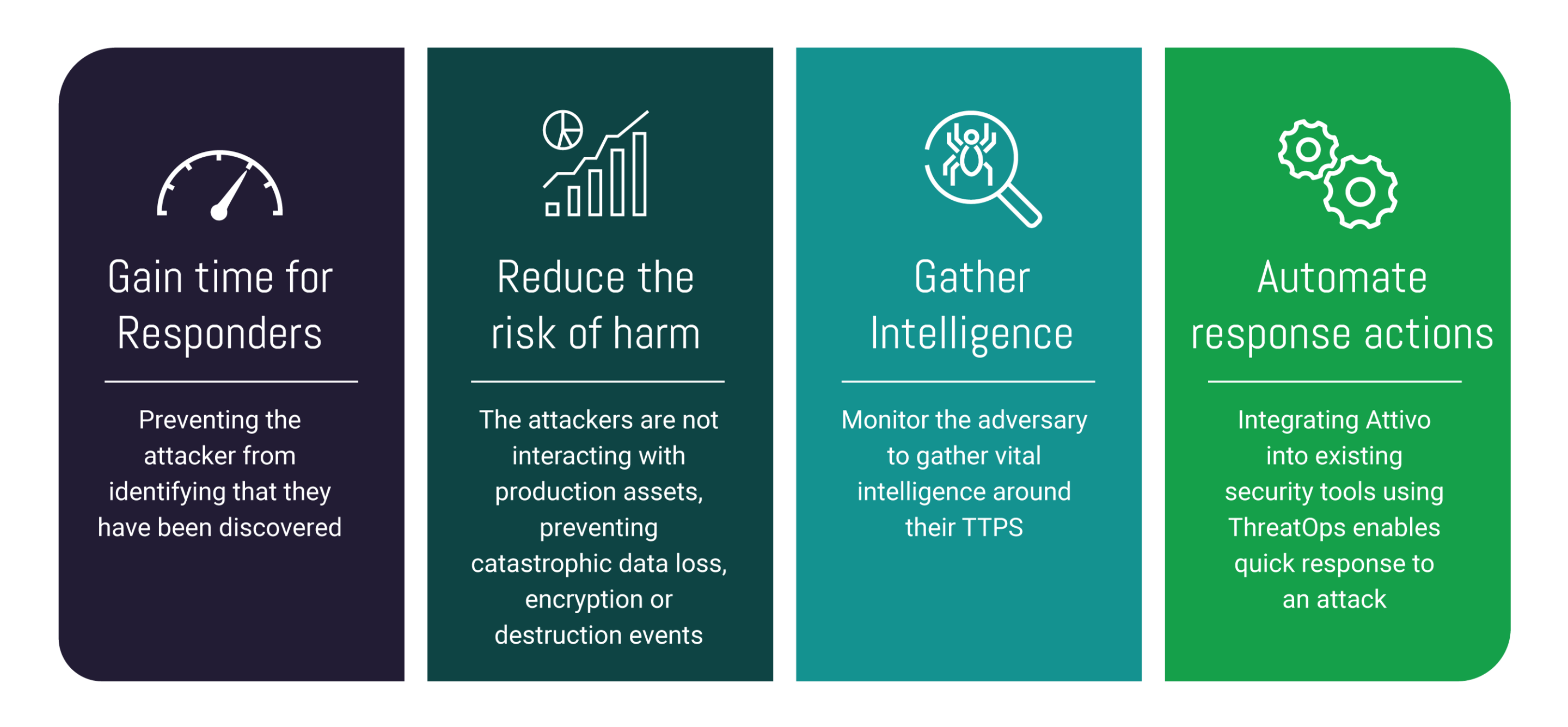
The attacker is therefore held in a state where they are unable to conduct malicious activities against live assets, giving the defending teams more time to deal with the threat.
Using the ThreatOps integrated connectors, our clients can deploy automated orchestration playbooks, enabling quick response actions to attacks, reducing MTTR and protecting critical data and assets.
Benefits Of Managed Active Defence
The Active Defence service significantly reduces the likelihood of an adversary completing their attack, leading to a data breach or other malicious action, as well as reducing the time to detect and respond to an incident. These metrics (known as Mean Time to Detect or MTTD and Mean Time to Respond or MTTR) are key indicators of an effective detect and respond capability.
The specific objectives of the service will be customised to each client collated through the BI workshops and service reviews on an ongoing basis. This is because every client faces different threats and operates a unique set of critical assets. LRQA Nettitude understands this and therefore can customise the detection through a unique set of use cases.
Managed Active Defence – Service Features
LRQA Nettitude’s Managed Active Defence service provides the most highly accredited expertise combined with Gartner Magic Quadrant leading security technology to deliver industry-leading protection for your organisation.
Our approach is proactive, and threat led; informed by our offensive and threat intelligence teams to shape our defensive stance. It protects against the latest industry threats to provide an in-depth defence with unrivalled detection and alerting capability where it is needed most.
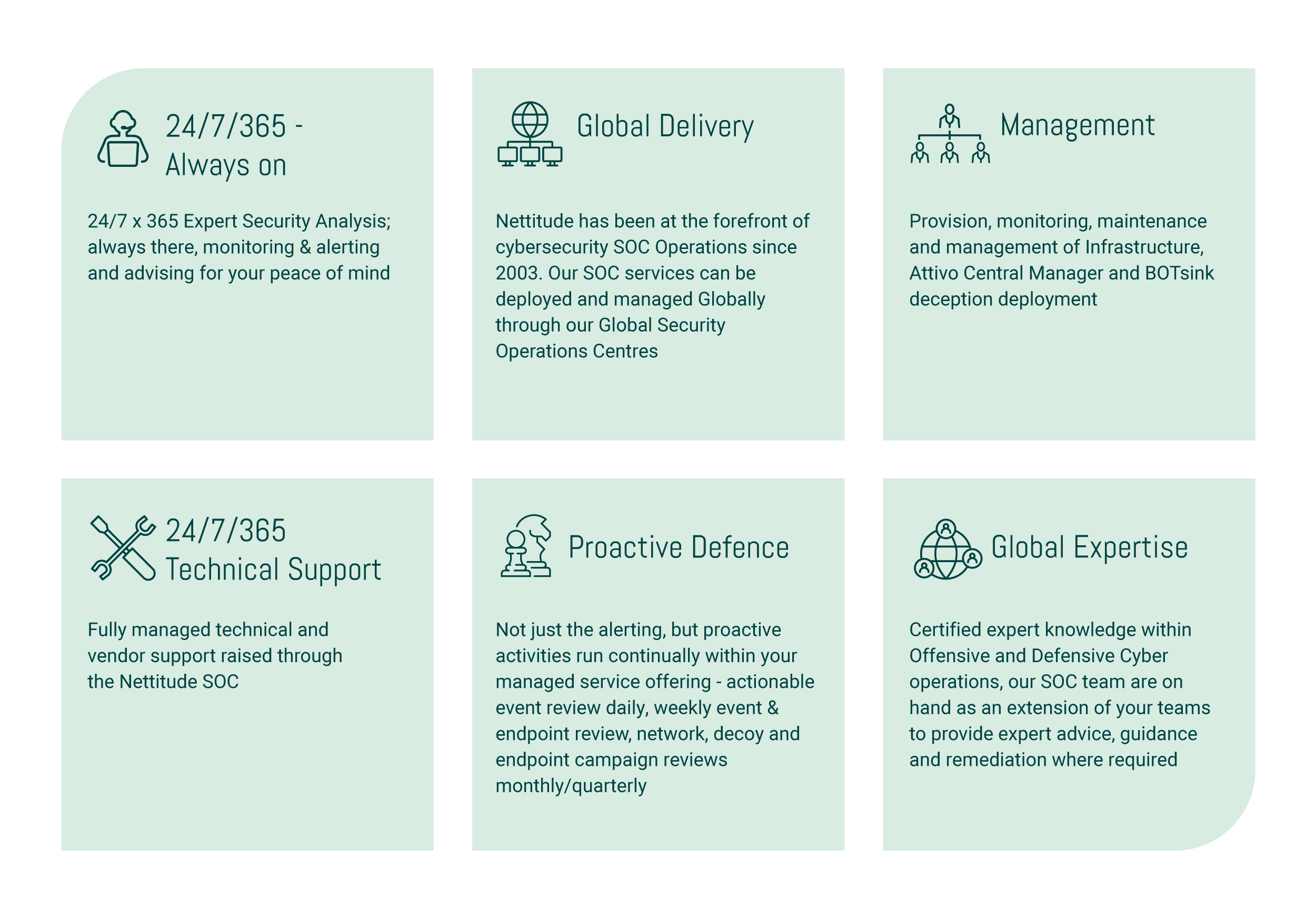
What our Managed Active Defence service includes
Actionable Event review – Performed 24/7 by LRQA Nettitude SOC team
Analysts daily (or often, multiple times a day as alerts are generated) review the events generated and recorded in the Attivo Central Manager system that are severity medium or higher. These events often contain information of an actionable nature and are the first line indication of malicious activity present on a company’s network.
Medium and higher severity events can indicate a severe network, server, or application misconfiguration which is causing multiple computing resources to communicate in an unhealthy or counter-productive manner (such as repeated ARP flooding and system scanning.)
In addition, these events are often directly related to policy violations, compromised computing systems, malicious software activity, or other security-related events. These events are meant to indicate activity that violates one or more policies on a network and should be investigated and mitigated appropriately.
System Health Check – Performed Daily by LRQA Nettitude SOC team
A daily system health check is performed for all Attivo systems, each product has a system status indicator to highlight when any warnings (yellow status) or critical errors (red status) are present on the Attivo system.
Clicking on the status indicator will provide analysts and system administrators with detailed information related to the status, which can be acknowledged, researched, or a support ticket opened to help resolve the issue.
Weekly Event Review – Performed Weekly by the LRQA Nettitude SOC team
Often performed weekly, analysts review the low and very low events recorded for the previous week to evaluate if any unexplained anomalies from a medium or higher event had any additional lower priority impact associated with that activity.
These events are often evaluated during the 24/7 actionable event review. However, lower-level events may appear before or after an actionable event and by performing a weekly review, may highlight other issues that can be investigated and mitigated. Note: low and very low events are not generally used for actionable event indicators as they are common on most networks. But they do provide context when higher priority events are identified. They may point to an in-depth context on an attack, misconfiguration, or a malicious event.
Weekly Endpoint Review – Performed Weekly by the LRQA Nettitude SOC team
Performed weekly, analysts review and check the endpoint reporting console to identify if any endpoints have been disconnected from the Attivo BOTsink or ACM.
They review Last Seen Date, comparing dates and times to the update interval defined for the Client Group Configuration setting. For example, if a client group has an update interval of 60 minutes, the Last Seen Date timestamp should be within the past 60 minutes. If any endpoints are found to be disconnected or not updated, that endpoint can be investigated to see if it is still online and able to communicate with the Attivo platform.
Where issues are discovered, these will be raised and managed by the LRQA Nettitude SOC team to the client’s technical teams to remediate.
Network, Decoy and Endpoint campaign review – Performed Monthly/Quarterly by Customer & LRQA Nettitude SOC Team – Recommended Quarterly by Vendor
On a monthly or quarterly basis, LRQA Nettitude and the client will perform a network segment and endpoint campaign review. The aim of this is to ensure that any network changes are captured and configured within the Threat Direct forwarder.
Endpoint campaign reviews are completed to ensure that decoy VM customisation (custom applications and services) are still relevant and to capture any changes. This could be new server VLANS on new network segments, for example. Any new requirements or new decoy deployments would then be scoped and deployed by the LRQA Nettitude SOC on behalf of the client.
Note: large scale changes and deployments of significant size or scope will require professional services time and effort.
Get a free quote











