Cyber incident response services
Ready for the inevitable?
Be prepared with an LRQA Nettitude incident response retainer
LRQA Nettitude provides a managed cyber incident response (IR) retainer tailored to suit the needs and threats your organisation could be facing.
Using leading industry technology and certified experts, the LRQA Nettitude cyber incident response team manages, contains, remediates, and reports on cyber incidents. Importantly, a managed cyber incident response retainer gives you assurance when you need it most.
£3,860,000 = The Average Data Breach Cost
+9 months = The Average Data Breach Resolution Time
The cost of an average data breach is £3.86 million while the average resolution time is 280 days. Proper incident response management helps reduce the impact of a cyber-breach by immediately sending triage to your organisation.
As cyber-threats evolve at pace around the world, the likes of ransomware, malware, and insider threats pose a serious risk to organisations. Especially when they go undetected for a while.
Once a breach is identified, time is of the essence and having experts on hand to control the damage is vital to getting your systems back on the road to recovery.
£3,860,000
The Average Data Breach Cost
+9 Months
The Average Data Breach Resolution Time
The cost of an average data breach is £3.86 million while the average resolution time is 280 days.
Proper incident response management helps reduce the impact of a cyber-breach by immediately sending triage to your organisation.
As cyber-threats evolve at pace around the world, the likes of ransomware, malware, and insider threats pose a serious risk to organisations. Especially when they go undetected for a while.
Once a breach is identified, time is of the essence and having experts on hand to control the damage is vital to getting your systems back on the road to recovery.
LRQA Nettitude named a Level 2 Cyber Incident Response Assured Service provider by NCSC and CREST
LRQA Nettitude is delighted to announce their status as a Level 2 National Cyber Security Centre (NCSC) Cyber Incident Response (CIR) Assured Service Provider.

LRQA Nettitude named a Level 2 Cyber Incident Response Assured Service provider by NCSC and CREST
LRQA Nettitude are delighted to announce their status as a Level 2 National Cyber Security Centre (NCSC) Cyber Incident Response (CIR) Assured Service Provider.

Benefits of a LRQA Nettitude cyber incident response retainer
Cyber incidents are only a matter of time. LRQA Nettitude’s experienced Cyber Incident Response Team (NCIRT) is committed to helping you at every stage of the incident response lifecycle. From preparation, eradication, and remediation, through to lessons learnt.
As part of our managed incident response, we provide a full range of tactical and strategic solutions tailored to your environment and organisational needs ensuring a robust security posture when you need it the most.
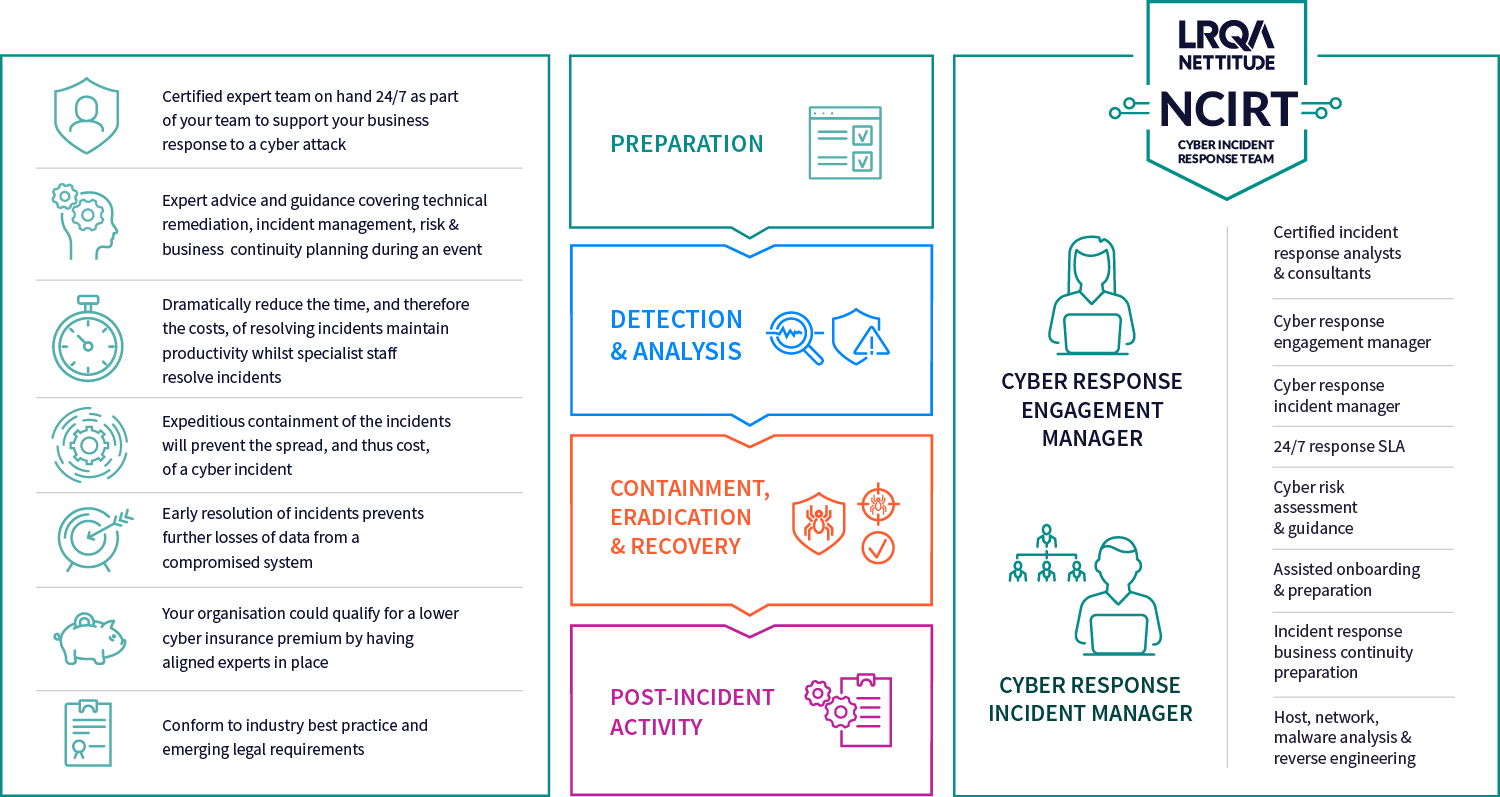
Incident response service features
We provide a full range of tactical and strategic solutions tailored to your environment and organisational needs ensuring a robust security posture when you need it the most. managed incident response is there to help you get back to normal operations quickly and with confidence.
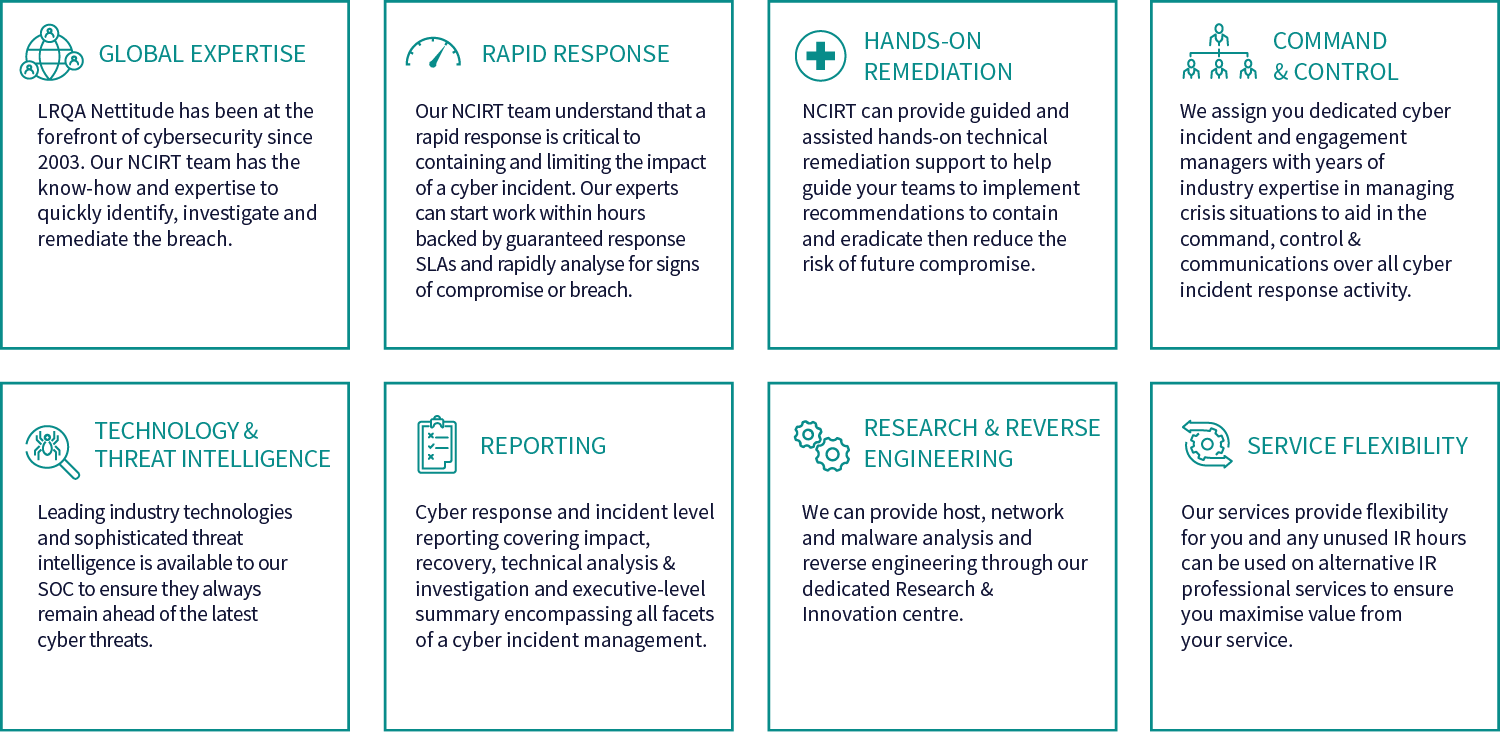
Incident response service options
LRQA Nettitude’s NCIRT works with you regardless of your budget, environment, or organisation size. We ensure you get the right care and readiness you need ranging from a basic IR consultation triage service to premium level services with guaranteed service level agreements (SLAs) and flexible consumption models.
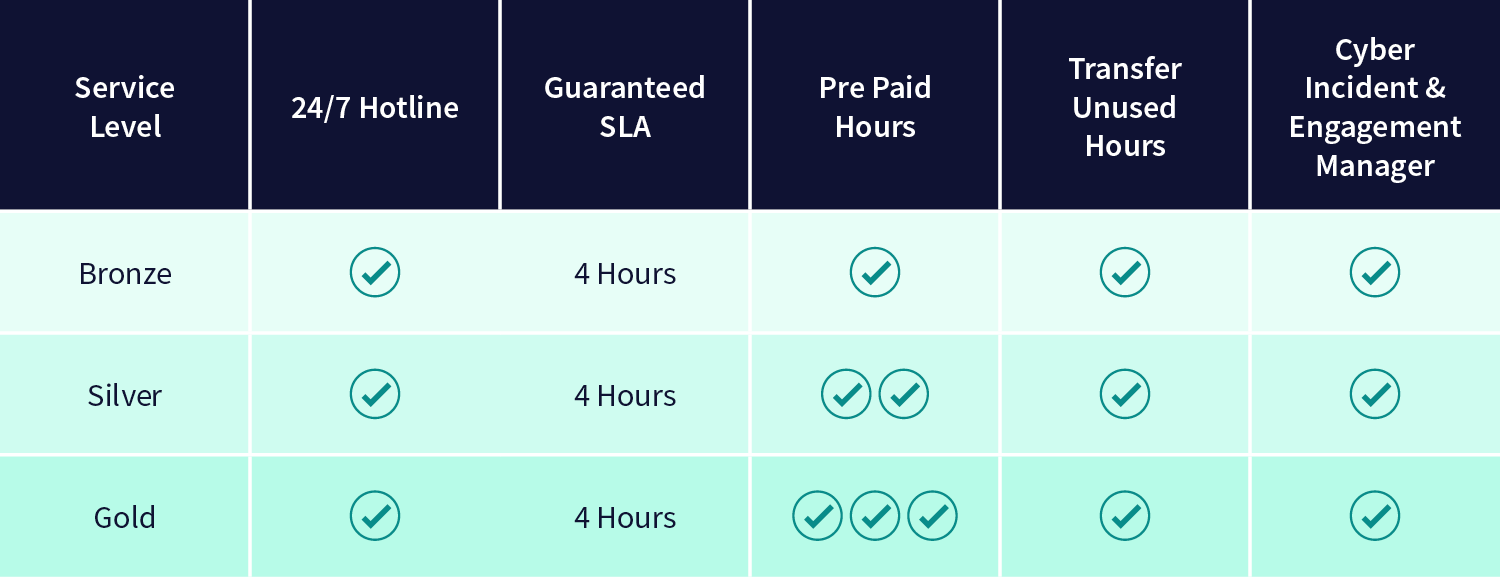

*Prepaid IR consult hours can only be used for IR triage hotline activity and not DFIR services
What is included?
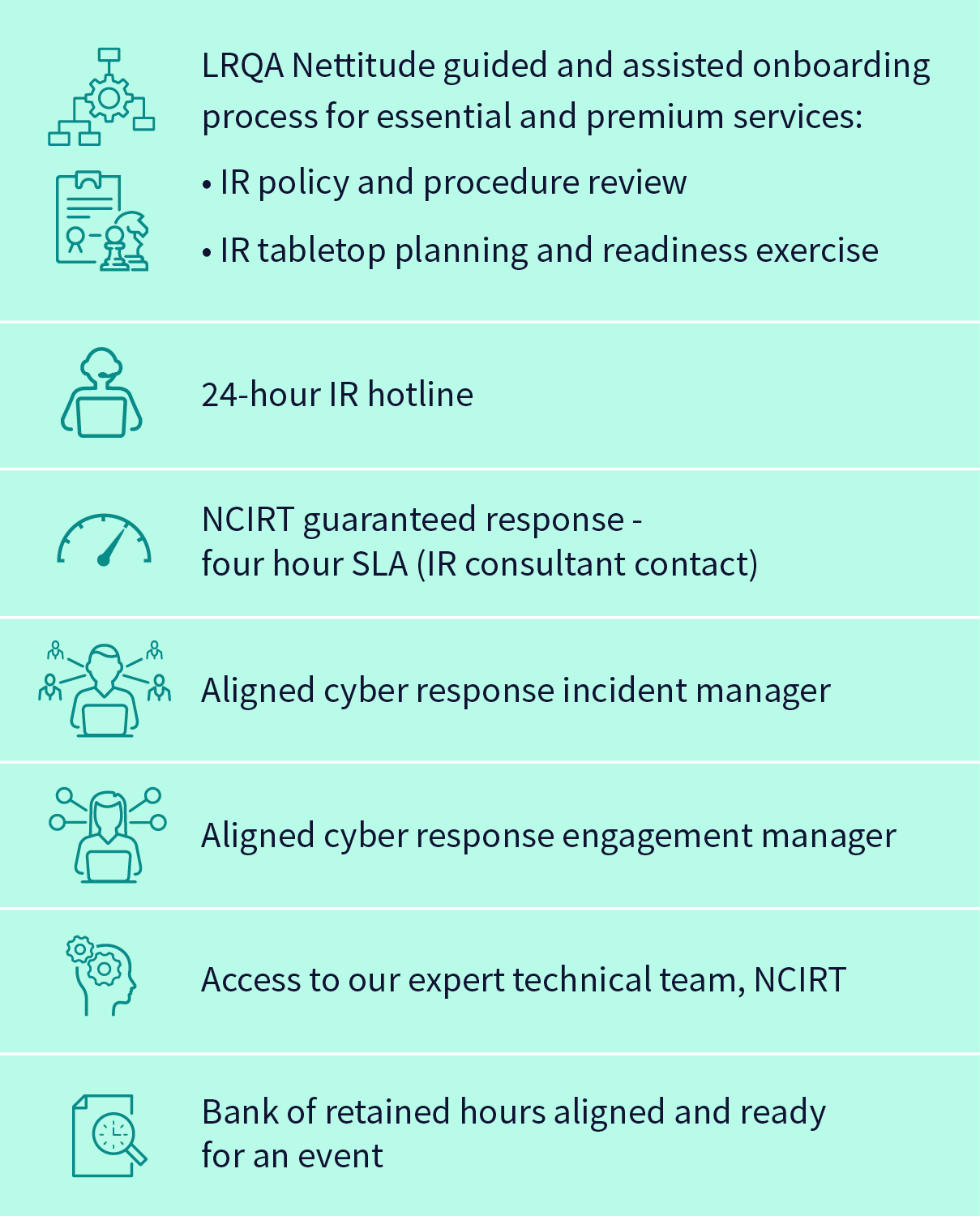

Proactive and professional services
LRQA Nettitude’s proactive incident response services help to evaluate your current incident response strategies and help you prepare no matter what stage or maturity level you are currently at. You can also use unused IR days against these proactive services ensuring you get the best value for your investment.


General Enquiry
General Enquiry





