

Technical Legacy Debt
Secures your legacy technology and provides ongoing protection
How do I prevent outdated software and systems from increasing our cybersecurity risk?
As your organization grows, you may find yourself relying on old software and systems.
While these programs may be familiar and comfortable to use, they can also pose serious cyber risks. Software and systems need to be evaluated and safeguarded.
The risks of using outdated software
Outdated software can make your business vulnerable to security breaches, data loss, and becoming non-compliant.
Package Approach
Our expert team will begin by evaluating your existing technology and legacy systems, then safeguard them with trusted advice and 24/7 monitoring.
Evaluation
• We provide expert capability across Infrastructure, Networks, Cloud, and applications with a detailed understanding of how vulnerabilities are compromised.
Advise
• We act as an extension of your team to technically remediate or mitigate the threats and vulnerabilities.
Continuous Monitoring
• Provision of services that support detection, protection, and response capability to cyber threats and vulnerabilities across your technologies and systems.
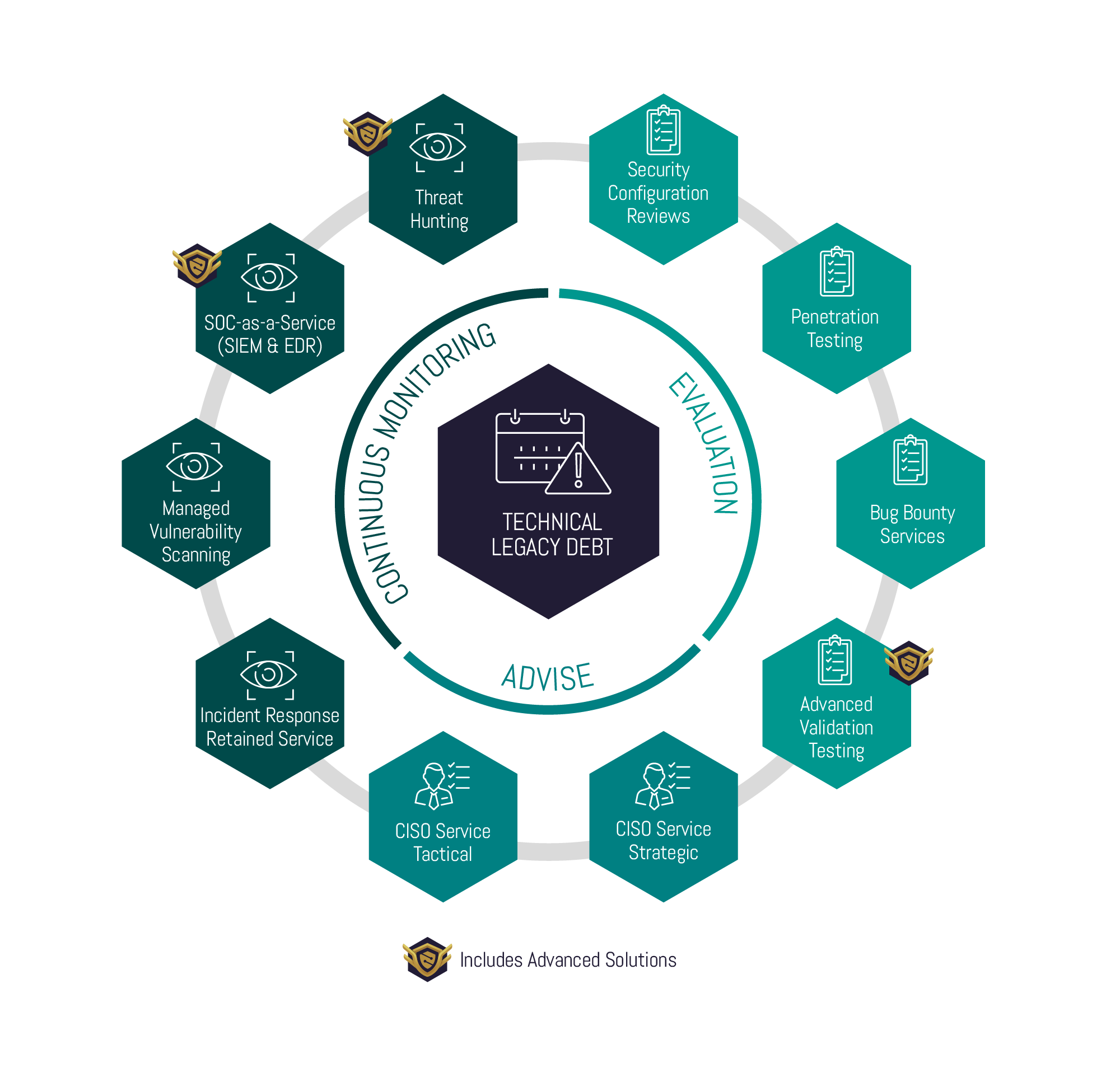
Choose our Technical Legacy Debt package
This package gives you peace of mind that your legacy technology is secure according to industry best practices. Going forward it gives you the added assurance of keeping your technology secure in the future.
The package is split into two offerings, Baseline and Advanced, select your package below.


Baseline Package
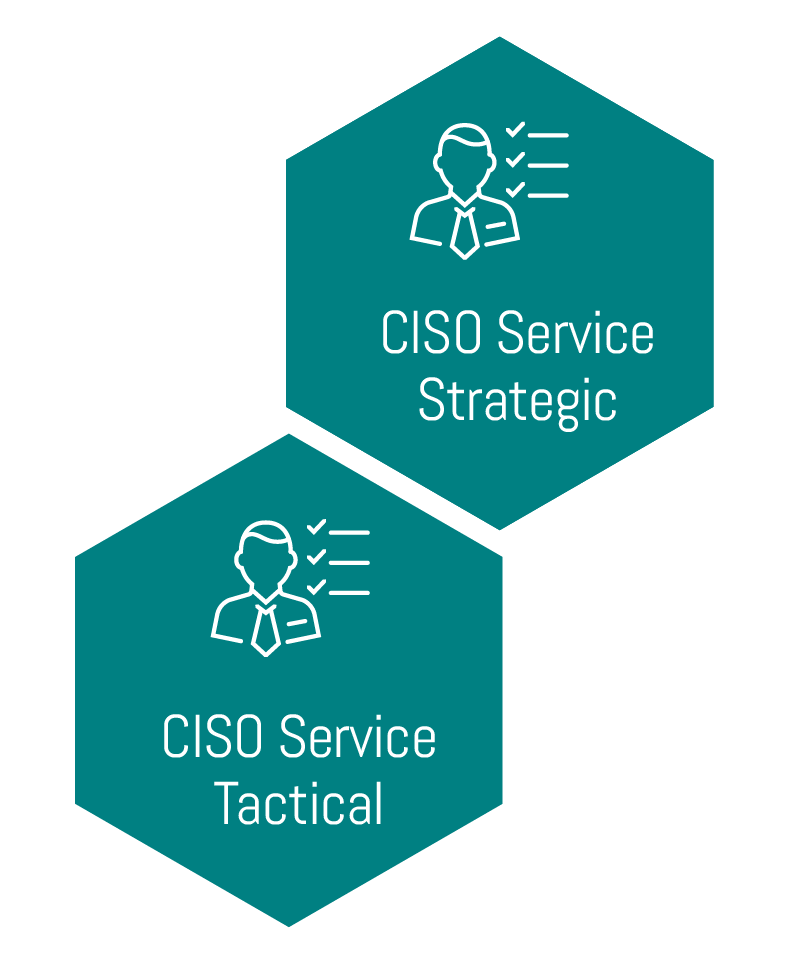
• CISO Service
A LRQA Nettitude security expert who can provide strategic and tactical guidance to your organisation and help develop and execute a security program to ensure your organisation’s information and technologies are protected from all cyber threats.
LRQA Nettitude’s CISO services help drive your organisation’s vision, strategy, and implementation to ensure you meet your information security objectives.
• Cyber Maturity Assessment
Quickly understand your organisation’s security posture to take risk-based decisions on improvement planning and budget and resource allocation.
Conducted through workshops, this service asks insightful and valuable questions that will enable a clear view of your cybersecurity needs and identifies any gaps and areas for improvement. Benchmarked against industry standards this assessment provides an external review and assurance of your organisation’s cyber maturity.
• Advisory Credits
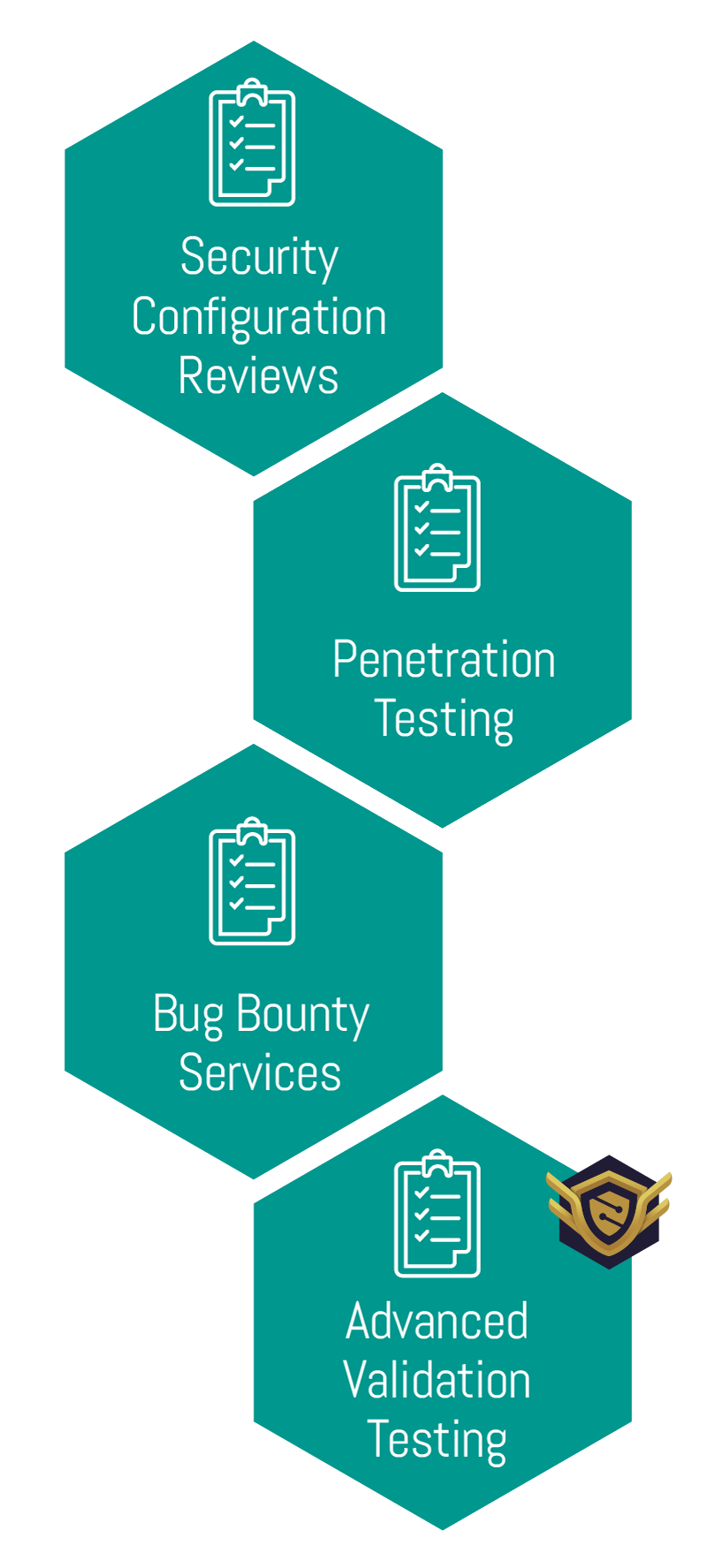
• Penetration Testing
A penetration test is an attempt to evaluate the security of your IT infrastructure through the safe exploitation of vulnerabilities via certified professionals. LRQA Nettitude specialises in the delivery of rigorous and strenuous security testing and provides you with a report on how attackers can exploit weaknesses in your infrastructure, networks, people, and processes.
• Bug Bounty
You pay us when we find issues, based on their criticality. We are always looking (same as the bad guys) and we will spend more time and resources looking deeper and wider into your systems that can be covered in a standard penetration test.
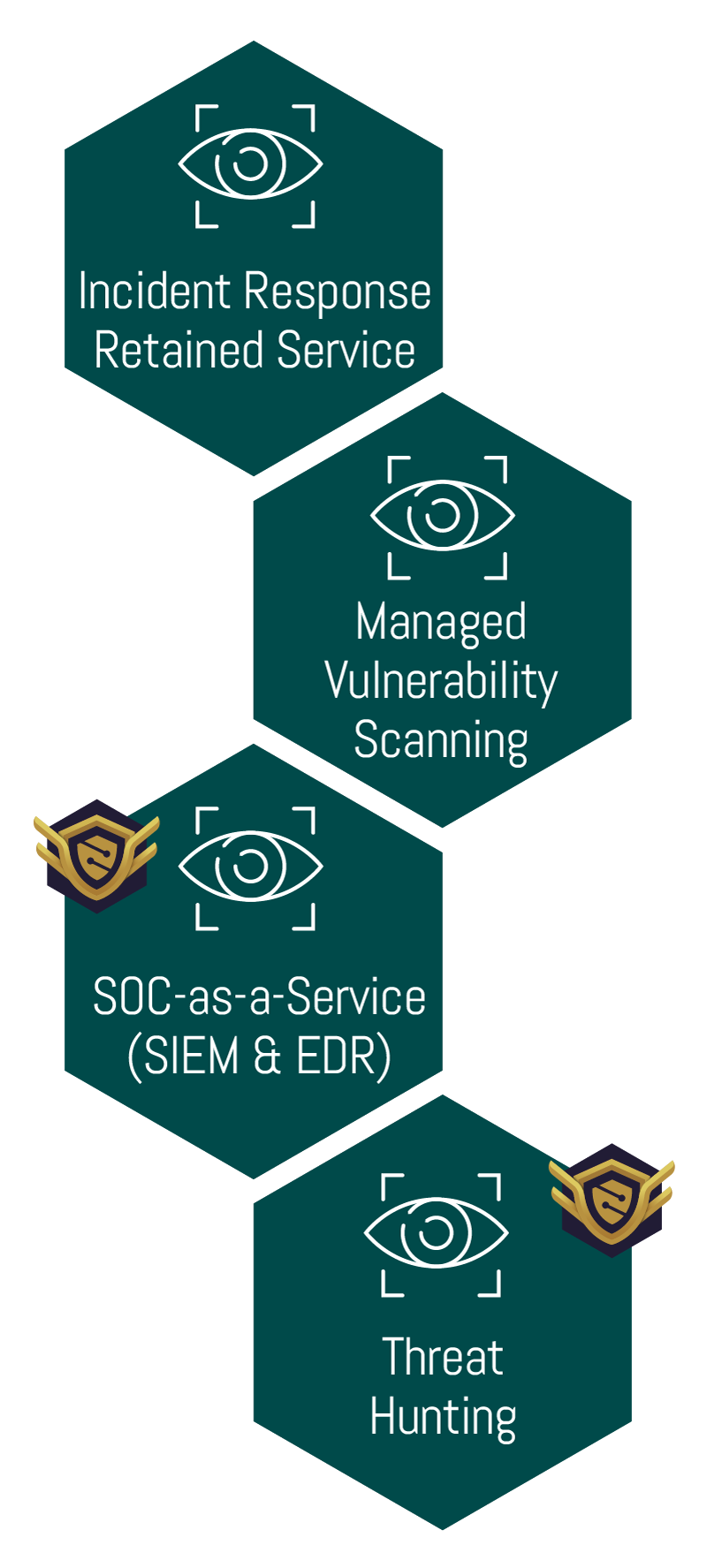
• Managed Vulnerability Scanning
Our Managed Vulnerability Scanning Service deploys a leading cloud-based vulnerability scanning and management technology to be able to identify, investigate, prioritise, mitigate, and respond to vulnerabilities within your environment and attack surface.
Understanding your risks as the number of vulnerabilities increases is critical in the current threat landscape. Managed Vulnerability Scanning is a fundamental component of any security testing programme for identifying existing or new vulnerabilities and misconfigurations across your systems.
LRQA Nettitude MVSS services have multiple customisable options tailored to fit your organisation that aid cyber maturity and risk-based methodologies to help you remediate and stay on top of critical issues and vulnerabilities that could leave you exposed.
Advanced Package
• CISO Service
A LRQA Nettitude security expert who can provide strategic and tactical guidance to your organisation and help develop and execute a security program to ensure your organisation’s information and technologies are protected from all cyber threats.
LRQA Nettitude’s CISO services help drive your organisation’s vision, strategy, and implementation to ensure you meet your information security objectives.
• Cyber Maturity Assessment
Quickly understand your organisation’s security posture to take risk-based decisions on improvement planning and budget and resource allocation.
Conducted through workshops, this service asks insightful and valuable questions that will enable a clear view of your cybersecurity needs and identifies any gaps and areas for improvement. Benchmarked against industry standards this assessment provides an external review and assurance of your organisation’s cyber maturity.
• Advisory Credits
• Penetration Testing
A penetration test is an attempt to evaluate the security of your IT infrastructure through the safe exploitation of vulnerabilities via certified professionals. LRQA Nettitude specialises in the delivery of rigorous and strenuous security testing and provides you with a report on how attackers can exploit weaknesses in your infrastructure, networks, people, and processes.
• Bug Bounty
You pay us when we find issues, based on their criticality. We are always looking (same as the bad guys) and we will spend more time and resources looking deeper and wider into your systems that can be covered in a standard penetration test.
• Managed Vulnerability Scanning
Deploys a leading cloud-based vulnerability scanning and management technology to identify, investigate, prioritise, mitigate, and respond to vulnerabilities within your environment.
Failing to understand and remediate the vulnerabilities within your environment could present an attacker with the opportunity they need to gain access to your systems.
• Purple Teaming
This is conducted as a joint exercise by the LRQA Nettitude Red Team (attackers) and Blue Team (defenders). This will improve your organisation’s security posture and increase resiliency to sophisticated attacks.
• Red Teaming
A Red team creates in-depth attack paths that mimic a wide range of sophisticated scenarios and inform you clearly of the current assurance levels around a cyber-attack.
• Managed Detection and Response
In today’s world, a SIEM solution combined with endpoint protection is becoming a necessity to be able to reduce the likelihood of an adversary attacking your organisation, leading to a data breach, Ransomware, or other malicious action against you.
SIEM and Endpoint Detection and Response (EDR) solutions are configured to be able to defend and alert against these malicious activities, helping to reduce the time to detect and respond to an incident.
• Managed Threat Hunting
The world of technology moves at a rapid pace and as such there are new techniques used by attackers to compromise organisations which may evade traditional detection solutions.
Our Threat Hunt-as-a-Service is provided using a mixture of sophisticated technology and highly certified threat hunters to provide assurance and identify whether your organisation is currently compromised, or even where historic compromise activity has occurred.
It understands the impact of any discovered breach and provides actionable guidance on the next steps to respond to and eradicate the threat.
Get in touch…
Explore More Cyber Packages…
Ransomware & Malware
How safe is your organization from a ransomware threat? Ensure you are always prepared for a ransomware or malware attack with this package.
Learn More…
Cyber Breach Readiness
Is your organization prepared for a cyber breach? This package prepares your organization and ensures you can respond to a breach.
Learn More…
Supplier & Third-Party Risk Management
Can you trust your supplier’s and third-parties cybersecurity? Select this package for complete assurance, governance, and risk management of your supply chain.
Learn More…
Penetration Testing Remediation
Penetration Tests have identified your weaknesses, but do you know how to remediate vulnerabilities? Select this package to ensure remediation is fully executed.
Learn More…
New Technology Cyber Risks
Concerned that moving to new technology will increase cyber risks? Choose this package for assurance that new technology is secured and protected by experts.
Learn More…
Technical Legacy Debt
Do you know legacy software systems can expose you to cyber threats? Ensure your systems are safe with this package to manage and secure legacy systems.
Learn More…


Technical Legacy Debt
Secures your legacy technology and provides ongoing protection
How do I prevent outdated software and systems from increasing our cybersecurity risk?
As your organization grows, you may find yourself relying on old software and systems.
While these programs may be familiar and comfortable to use, they can also pose serious cyber risks. Software and systems need to be evaluated and safeguarded.
The risks of using outdated software
Outdated software can make your business vulnerable to security breaches, data loss, and becoming non-compliant.
Package Approach
Our expert team will begin by evaluating your existing technology and legacy systems, then safeguard them with trusted advice and 24/7 monitoring.
Evaluation
We provide expert capability across Infrastructure, Networks, Cloud, and applications with a detailed understanding of how vulnerabilities are compromised.
Advise
We act as an extension of your team to technically remediate or mitigate the threats and vulnerabilities.
Continuous Monitoring
Provision of services that support detection, protection, and response capability to cyber threats and vulnerabilities across your technologies and systems.
Choose our Technical Legacy Debt package
This package gives you peace of mind that your legacy technology is secure according to industry best practices. Going forward it gives you the added assurance of keeping your technology secure in the future.
The package is split into two offerings, Baseline and Advanced, select your package below.

Baseline Package
• CISO Service
A LRQA Nettitude security expert who can provide strategic and tactical guidance to your organisation and help develop and execute a security program to ensure your organisation’s information and technologies are protected from all cyber threats.
LRQA Nettitude’s CISO services help drive your organisation’s vision, strategy, and implementation to ensure you meet your information security objectives.
• Cyber Maturity Assessment
Quickly understand your organisation’s security posture to take risk-based decisions on improvement planning and budget and resource allocation.
Conducted through workshops, this service asks insightful and valuable questions that will enable a clear view of your cybersecurity needs and identifies any gaps and areas for improvement. Benchmarked against industry standards this assessment provides an external review and assurance of your organisation’s cyber maturity.
• Advisory Credits
Advisory Credits give you the ability to obtain one of LRQA Nettitude’s advisory services.
• Penetration Testing
A penetration test is an attempt to evaluate the security of your IT infrastructure through the safe exploitation of vulnerabilities via certified professionals. LRQA Nettitude specialises in the delivery of rigorous and strenuous security testing and provides you with a report on how attackers can exploit weaknesses in your infrastructure, networks, people, and processes.
• Bug Bounty
You pay us when we find issues, based on their criticality. We are always looking (same as the bad guys) and we will spend more time and resources looking deeper and wider into your systems that can be covered in a standard penetration test.
• Managed Vulnerability Scanning
Our Managed Vulnerability Scanning Service deploys a leading cloud-based vulnerability scanning and management technology to be able to identify, investigate, prioritise, mitigate, and respond to vulnerabilities within your environment and attack surface.
Understanding your risks as the number of vulnerabilities increases is critical in the current threat landscape. Managed Vulnerability Scanning is a fundamental component of any security testing programme for identifying existing or new vulnerabilities and misconfigurations across your systems.
LRQA Nettitude MVSS services have multiple customisable options tailored to fit your organisation that aid cyber maturity and risk-based methodologies to help you remediate and stay on top of critical issues and vulnerabilities that could leave you exposed.

Advanced Package
• CISO Service
A LRQA Nettitude security expert who can provide strategic and tactical guidance to your organisation and help develop and execute a security program to ensure your organisation’s information and technologies are protected from all cyber threats.
LRQA Nettitude’s CISO services help drive your organisation’s vision, strategy, and implementation to ensure you meet your information security objectives.
• Cyber Maturity Assessment
Quickly understand your organisation’s security posture to take risk-based decisions on improvement planning and budget and resource allocation.
Conducted through workshops, this service asks insightful and valuable questions that will enable a clear view of your cybersecurity needs and identifies any gaps and areas for improvement. Benchmarked against industry standards this assessment provides an external review and assurance of your organisation’s cyber maturity.
• Advisory Credits
• Penetration Testing
A penetration test is an attempt to evaluate the security of your IT infrastructure through the safe exploitation of vulnerabilities via certified professionals. LRQA Nettitude specialises in the delivery of rigorous and strenuous security testing and provides you with a report on how attackers can exploit weaknesses in your infrastructure, networks, people, and processes.
• Bug Bounty
You pay us when we find issues, based on their criticality. We are always looking (same as the bad guys) and we will spend more time and resources looking deeper and wider into your systems that can be covered in a standard penetration test.
• Managed Vulnerability Scanning
Deploys a leading cloud-based vulnerability scanning and management technology to identify, investigate, prioritise, mitigate, and respond to vulnerabilities within your environment.
Failing to understand and remediate the vulnerabilities within your environment could present an attacker with the opportunity they need to gain access to your systems.
• Purple Teaming
Purple Teaming exercises simulate specific attack scenarios to ensure your organisation is prepared to detect and respond in the real world.
This is conducted as a joint exercise by the LRQA Nettitude Red Team (attackers) and Blue Team (defenders). This will improve your organisation’s security posture and increase resiliency to sophisticated attacks.
• Red Teaming
A Red team creates in-depth attack paths that mimic a wide range of sophisticated scenarios and inform you clearly of the current assurance levels around a cyber-attack.
• Managed Detection and Response
In today’s world, a SIEM solution combined with endpoint protection is becoming a necessity to be able to reduce the likelihood of an adversary attacking your organisation, leading to a data breach, Ransomware, or other malicious action against you.
SIEM and Endpoint Detection and Response (EDR) solutions are configured to be able to defend and alert against these malicious activities, helping to reduce the time to detect and respond to an incident.
• Managed Threat Hunting
Our Threat Hunt-as-a-Service is provided using a mixture of sophisticated technology and highly certified threat hunters to provide assurance and identify whether your organisation is currently compromised, or even where historic compromise activity has occurred.
It understands the impact of any discovered breach and provides actionable guidance on the next steps to respond to and eradicate the threat.
Get in touch…
Discover the Cyber Package that solves your top security concern below
Ransomware & Malware
How safe is your organization from a ransomware threat? Ensure you are always prepared for a ransomware or malware attack with this package.
Learn More…
Cyber Breach Readiness
Is your organization prepared for a cyber breach? This package prepares your organization and ensures you can respond to a breach.
Learn More…
Supplier & Third-Party Risk Management
Can you trust your supplier’s and third-parties cybersecurity? Select this package for complete assurance, governance, and risk management of your supply chain.
Learn More…
Employee Security & Training
Concerned about how to protect against threats that target employees? This package will secure and train employees while monitoring the threats they face.
Learn More…
Penetration Testing Remediation
Penetration Tests have identified your weaknesses, but do you know how to remediate vulnerabilities? Select this package to ensure remediation is fully executed.
Learn More…
New Technology Cyber Risks
Concerned that moving to new technology will increase cyber risks? Choose this package for assurance that new technology is secured and protected by experts.
Learn More…
Technical Legacy Debt
Do you know legacy software systems can expose you to cyber threats? Ensure your systems are safe with this package to manage and secure legacy systems.
Learn More…
Develop a Cybersecurity Programme
Can you prevent, withstand, and recover from cyber incidents? This package builds a cyber strategy equipping you against evolving threats.
Learn More…
Explore More Cyber Packages…
Ransomware & Malware
How safe is your organization from a ransomware threat? Ensure you are always prepared for a ransomware or malware attack with this package.
Learn More…
Cyber Breach Readiness
Is your organization prepared for a cyber breach? This package prepares your organization and ensures you can respond to a breach.
Learn More…
Supplier & Third-Party Risk Management
Can you trust your supplier’s and third-parties cybersecurity? Select this package for complete assurance, governance, and risk management of your supply chain.
Learn More…
Employee Security &
Training
Concerned about how to protect against threats that target employees? This package will secure and train employees while monitoring the threats they face.
Learn More…
Penetration Testing Remediation
Penetration Tests have identified your weaknesses, but do you know how to remediate vulnerabilities? Select this package to ensure remediation is fully executed.
Learn More…
New Technology
Cyber Risks
Concerned that moving to new technology will increase cyber risks? Choose this package for assurance that new technology is secured and protected by experts.
Learn More…

Develop a Cybersecurity Programme
Can you prevent, withstand, and recover from cyber incidents? This package builds a cyber strategy equipping you against evolving threats.
Learn More…











