CMMC Compliance Consulting
While CMMC compliance may be new ground for your organization, it’s familiar territory for our CMMC consultants who are all certified CMMC Registered Practitioners (RPs). We begin with a CMMC gap assessment, issuing a report that identifies weaknesses and provides a roadmap to compliance. We then drive remediation through a set of activities customized to the client’s specific needs.
As an accredited CMMC Registered Provider Organization (RPO), we follow up with a comprehensive CMMC pre-assessment to determine the organization’s readiness for an official CMMC assessment. Finally, we prepare the client for the assessment and then manage the assessment on their behalf.
How close is your organization to being CMMC compliant?
Audits can be very humbling, particularly for organizations that consider themselves to be diligent, only to learn that they’re falling short in numerous key areas. Sometimes it’s a case where you need to step away from the forest to see the trees. Other times you just need a second set of eyes from someone familiar with the territory. That’s where LRQA Nettitude can help.
Our CMMC compliance consultants take the time to get to know your organization: Who you are, what you’re doing well, and where you need some help. We understand that though security is a critical aspect of your job, the pressure to keep the business up and running can pull your attention away from addressing cyber risks. Our CMMC consulting begins by identifying where you are. We then give you a roadmap to where you want to be.
What is CMMC?
The Cybersecurity Maturity Model Certification (CMMC) is a comprehensive cyber risk management model comprised of 17 domains that measure an organization’s capabilities against 5 cybersecurity maturity levels where the most basic level is Level 1 and the most advanced is Level 5. It was developed by the U.S. Department of Defense (DoD) to establish cybersecurity standards for suppliers who handle Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). CMMC builds upon NIST 800-171 which defined mandatory security requirements that organizations must self-assess against. CMMC offers a higher level of assurance than NIST 800-171 since it requires organizations to undergo an assessment conducted by a Certified Third-Party Assessment Organizations (C3PAO).
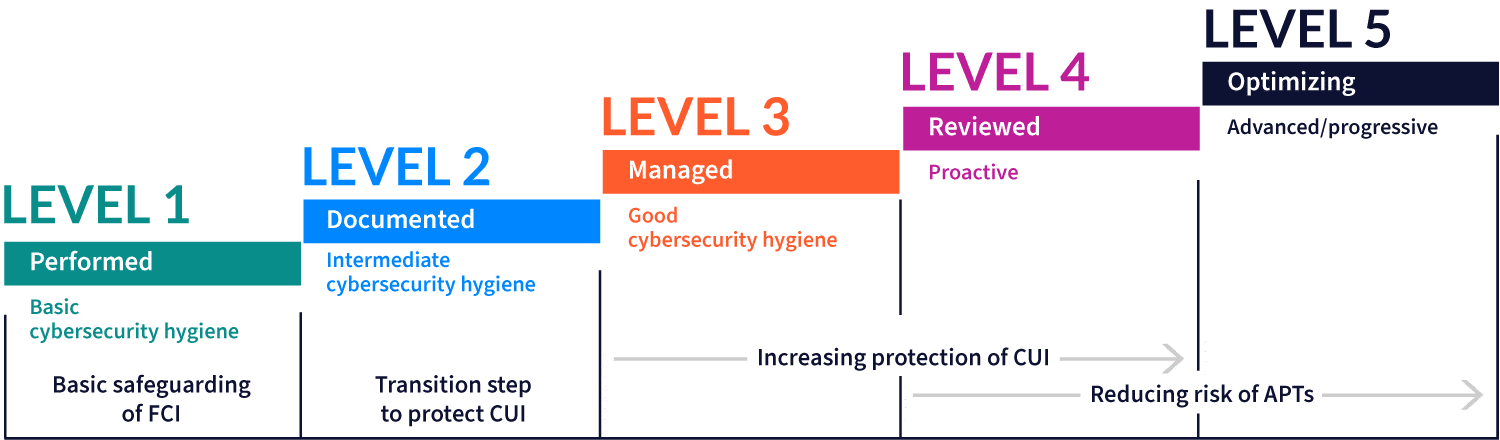
The nature of the data that a supplier will handle in their work will determine the maturity level that the supplier must certify against. For instance, projects involving only FCI will just require Level 1 certification, while projects involving CUI will require Level 3 certification at a minimum. Levels 4 and 5 certification is to identify organizations that are capable of effectively reducing the risk presented by Advanced Persistent Threats (APTs).
Being a massive undertaking, the CMMC Accreditation Body (CMMC AB) is implementing the CMMC program in phases with the current focus on certifying select suppliers against Levels 1 through 3. The number of organizations requiring CMMC certification will increase in the ensuing years until 2026 when all suppliers handling FCI and CUI must have the appropriate level of certification.
C3PAOs will conduct the certification assessments and recommend either certifying the organization or denying certification to the CMMAC AB which is responsible for conferring certification. RPOs, on the other hand, while not conducting official assessments are accredited by the CMMC AB to conduct CMMC pre-assessments that fully align with an official CMMC assessment. LRQA Nettitude is an RPO and as such we offer a range of services from gap analyses to pre-assessments and full-scope CMMC implementation support where we provide the expertise that an organization may lack in-house.
Advantages of advanced CMMC preparation
Given the phased implementation, there’s a strong temptation to put off CMMC preparation until the organization has a firm certification deadline. However, advanced preparation has numerous advantages including:
- A positive CMMC pre-assessment report issued by an RPO can be a powerful differentiator as the report provides clients with a level of assurance of the organization’s capabilities.
- Identifying gaps early on enables an organization to develop a strategy for investing in resources and effort to achieve CMMC certification when it is required.
- It’s the right thing to do right now because the organization will have a framework for building a robust cybersecurity program that will yield results in the near term benefiting clients across all sectors.
In short, by aligning its practices to CMMC compliance requirements, an organization will become more operationally mature, because its approach will evolve from ad-hoc crisis management to methodical vulnerability reduction and efficient incident management.
Ways we can help you with CMMC compliance
Developing an organization’s cybersecurity maturity is a long-term commitment that is best carried out in phases. Below is a breakdown of those phases paired with services that LRQA Nettitude offers to achieve the objectives of each phase.
- Gap analysis
- Reporting
- Debrief and roadmap
- Remediation and strategy
- Implementation support
- Pre-assessment
- Audit support
CMMC consulting phases
Discovery
In this phase, the organization identifies areas where it falls short and what it needs to do to meet applicable CMMC requirements. The emphasis in this phase is on assessing practice maturity as opposed to process maturity. See ‘Steps to CMMC Compliance’ to understand the distinction between practice and process maturity.
- CMMC gap analysis: Applicable CMMC requirements are identified based on the maturity level that the client seeks to achieve. The LRQA Nettitude Registered Practitioner (RP) identifies gaps in practices through a series of interviews and reviews of documents and evidentiary artefacts.
- Compliance Roadmap: With an emphasis on closing the identified gaps, the LRQA Nettitude RP provide an organized body of recommendations on practice improvements and remediation activities in a format consistent with a Plan of Action and Milestones (PoAM).
The LRQA Nettitude RP consolidates findings in a single gap analysis and compliance roadmap report suitable for executive leadership (dashboards) and operational team members (task lists).
Corrective actions
This phase focuses on closing the gaps in practices identified in the discovery phase. The LRQA Nettitude RP help develop the client’s process maturity as needed for CMMC Level 3 certification.
Remediation strategy and oversight: The LRQA Nettitude RP leverage the CMMC gap analysis and compliance roadmap report to drive a gap remediation program. In this effort, the RP will:
- Support project management of the remediation program
- Consult on the most effective corrective measures to meet requirements
- Report on the progress to senior management and executive stakeholders
Full scope CMMC implementation support
As a cybersecurity consultancy, LRQA Nettitude has a wide range of experts capable of fulfilling any roles where our clients may need support. Services we offer clients to quickly evolve their cybersecurity posture include:
- Virtual CISO
- Security Operations Center (SOC)
- Network architecture and configuration management (including firewall review)
- Penetration testing
- Documentation development (policies, procedures, standards and plan for the maintenance of domain capabilities)
If you have already moved other business-critical functions such as CRM, payroll, and data processing to the cloud, why should your SIEM be any different? LogRhythm Axon excels at cloud-to-cloud log collection and is ready to go out of the box, with content mapped to the MITRE ATT&CK® framework.
Assessment preparation
The corrective action phase is completed when all gaps identified in the discovery phase have been closed. In the Assessment Preparation phase, the LRQA Nettitude RP lays the groundwork for a successful CMMC assessment in the same way that we prepare our clients for successful audits against other frameworks like ISO 27001 and PCI DSS.
- Pre-assessment: A LRQA Nettitude RP will conduct a full-scope CMMC pre-assessment that directly reflects the approach and techniques that the C3PAO will utilize in the official CMMC assessment because the RP has been trained directly by the CMMC AB on conducting an assessment in a manner that aligns with CMMC AB requirements.
- Pre-assessment report: The LRQA Nettitude RP will issue a comprehensive report that identifies any CMMC practices and process requirements that are not fully met and offers recommendations on addressing each deficiency.
Audit preparation and management
Similar to the remediation strategy and oversight services offered during the corrective action phase, the LRQA Nettitude RP will oversee the effort to remediate any remaining deficiencies identified in the Pre-Assessment. In this capacity, the LRQA Nettitude RP will:
- Will track progress and report on efforts to remediate deficiencies
- Advice on when the organization is ready for an official assessment
- Organize evidentiary material in a manner that will enable the C3PAO assessor to find the required information in the most efficient manner possible
During the audit, the LRQA Nettitude RP will support or manage the client’s response to the audit by:
- Attending the Assessment kickoff meeting and walking the assessor through the structure of the evidence repository and identifying relevant stakeholders and subject matter experts (SMEs)
- Coordinating the scheduling of assessor interviews of executive stakeholders and SMEs
- Preparing executive stakeholders and SMEs in responding to assessor inquiries
Steps to CMMC compliance
Many organizations have pockets of strong practices but also have gaps elsewhere in their business. Such organizations would be considered to have low practice maturity. Other organizations may have relatively high practice maturity but lack process maturity because practices are carried out ad-hoc where little is documented. Process maturity supports the resilience of practices by documenting not only the methods for implementing required practices but also the plan for maintaining the practices over the long haul. Fortunately, practice maturity and process maturity can be developed in parallel. The table depicts these parallel paths to CMMC maturity.
Practice maturity
For each practice the following activities must be undertaken:
- Identify gaps,
- Develop a remediation program with a strategy for each gap,
- Remediate and track progress,
- Conduct a re-assessment,
- Remediate and determine readiness date for certification assessment.
Process maturity
For each in-scope practice there must be:
- A policy that delineates applicable practice requirements,
- Supporting documents for meeting each policy requirement (e.g. procedures and standards).
For each CMMC domain to maintain applicable capabilities. This plan would address such considerations as:
- Mission and objectives,
- Relevant standards and procedures,
- Required skills and tools,
- Budgetary requirements.
After addressing all the elements enumerated in the table above, conduct an accredited CMMC pre-assessment to confirm readiness for an official assessment. Then, prepare for that assessment.
CMMC Compliance Consulting
While CMMC compliance may be new ground for your organization, it’s familiar territory for our CMMC consultants who are all certified CMMC Registered Practitioners (RPs). We begin with a CMMC gap assessment, issuing a report that identifies weaknesses and provides a roadmap to compliance. We then drive remediation through a set of activities customized to the client’s specific needs.
How close is your organisation to being CMMC compliant?
Audits can be very humbling, particularly for organizations that consider themselves to be diligent, only to learn that they’re falling short in numerous key areas. Sometimes it’s a case where you need to step away from the forest to see the trees. Other times you just need a second set of eyes from someone familiar with the territory. That’s where LRQA Nettitude can help.
Our CMMC compliance consultants take the time to get to know your organization: Who you are, what you’re doing well, and where you need some help. We understand that though security is a critical aspect of your job, the pressure to keep the business up and running can pull your attention away from addressing cyber risks.
Our CMMC consulting begins by identifying where you are. We then give you a roadmap to where you want to be.
What is CMMC?
The Cybersecurity Maturity Model Certification (CMMC) is a comprehensive cyber risk management model comprised of 17 domains that measure an organization’s capabilities against 5 cybersecurity maturity levels where the most basic level is Level 1 and the most advanced is Level 5.
It was developed by the U.S. Department of Defense (DoD) to establish cybersecurity standards for suppliers who handle Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
CMMC builds upon NIST 800-171 which defined mandatory security requirements that organizations must self-assess against. CMMC offers a higher level of assurance than NIST 800-171 since it requires organizations to undergo an assessment conducted by a Certified Third-Party Assessment Organizations (C3PAO).
Ways we can help you with CMMC compliance
Developing an organization’s cybersecurity maturity is a long-term commitment that is best carried out in phases. Below is a breakdown of those phases paired with services that LRQA Nettitude offers to achieve the objectives of each phase.
- Gap analysis
- Reporting
- Debrief and roadmap
- Remediation and strategy
- Implementation support
- Pre-assessment
- Audit support
Steps to CMMC compliance
Many organizations have pockets of strong practices but also have gaps elsewhere in their business. Such organizations would be considered to have low practice maturity.
Other organizations may have relatively high practice maturity but lack process maturity because practices are carried out ad-hoc where little is documented. Process maturity supports the resilience of practices by documenting not only the methods for implementing required practices but also the plan for maintaining the practices over the long haul.
Fortunately, practice maturity and process maturity can be developed in parallel. The table depicts these parallel paths to CMMC maturity.
Practice maturity
For each practice the following activities must be undertaken:
- Identify gaps,
- Develop a remediation program with a strategy for each gap,
- Remediate and track progress,
- Conduct a re-assessment,
- Remediate and determine readiness date for certification assessment.
Process maturity
For each in-scope practice there must be:
- A policy that delineates applicable practice requirements,
- Supporting documents for meeting each policy requirement (e.g. procedures and standards).
For each CMMC domain to maintain applicable capabilities. This plan would address such considerations as:
- Mission and objectives,
- Relevant standards and procedures,
- Required skills and tools,
- Budgetary requirements.
After addressing all the elements enumerated in the table above, conduct an accredited CMMC pre-assessment to confirm readiness for an official assessment. Then, prepare for that assessment.
Protect your Organization with LRQA Nettitude’s
Award-Winning Cybersecurity Services
Speak to one of our cybersecurity experts now…
Protect your Organization with LRQA Nettitude’s Award-Winning Cybersecurity Services
Speak to one of our cybersecurity experts now…





