Breaches happen
What matters is how you respond to them
LRQA Nettitude have been preparing organizations for, responding to, and managing cyber incidents across three continents for over 20 years.
Are you prepared for a cyber incident?
Get immediate assistance
If you know, or even just suspect you are experiencing a cyber incident then time is of the essence.
Get immediate assistance…
Incident Response
Our incident response management helps reduce the impact of a cyber-breach by immediately sending assistance to your organization. We only work with and deploy leading incident response technologies including:



Why is a rapid and thorough response essential?
- Preventing the spread will reduce the cost of recovery
- It will reduce the recovery time required
- Increase the likelihood that more parts of your business will be able to function as normal during remediation
“LRQA Nettitude’s early advice prevented a full deployment of ransomware malware across our entire IT network. Their timely response and investigation enabled the business to reduce the impact of the breach and continue operations.
We are the only organization in the world with a full suite of CREST accreditations
Our Incident Response Team includes:
- CREST Registered Intrusion Analysts
- CREST Certified Network Intrusion Analysts
- CREST Certified Malware Reverse Engineers
Prepare your incident response plan
• Organizations who are prepared with an incident response team that stress test their cyber plans save $2.4 million versus those who do not
• 77% of cybersecurity leaders say the number of attacks against their company has increased since 2021
We only work with and deploy leading incident response technologies including:



Companies who prepare better, perform better.
Knowing how to detect a cybersecurity breach and having a response plan in place are essential fundamentals for any organization. This means engaging with the right people, with the right skills, who have access to the right tools on hand 24/7/365. We can drill and regularly test your internal teams to ensure they know the procedures to follow to contain and remediate a cyber incident.
“We are now in a much stronger position to detect and respond to attacks. Sentinel is fully deployed and monitoring the IT estate, and the whole business is now taking a much more mature approach to cybersecurity. The executive team now have the assurance that the business is prepared for further attacks and will be able to respond appropriately.”
Book an incident response demo…
Providing value for our global clients
A programme of this magnitude is complex and difficult to administer in terms of staff turnover, training, and sourcing/integrating the right tools. This is where LRQA Nettitude provides value for our global clients.
Introducing NCIRT
Our incident response team are highly trained, experienced, and committed to helping you at every stage of the incident response lifecycle. From preparation and eradication, through to remediation and lessons learnt we are available 24/7/365.
Case study
Read about how LRQA Nettitude provided urgent incident response services to a multinational online retailer who realised their IT network had been compromised.
Managed SIEM solution
• Only 28% of organizations integrate their security controls into a security information and event management (SIEM)/security orchestration, automation, and response (SOAR) platform to orchestrate their response to an attack.
• SIEM solutions can deliver an excellent ROI. A recent Forrester study showed a 258% ROI for clients with the investment paying for itself in less than six months.
We only work with and deploy leading incident response technologies including:




Immediate results
It is increasingly difficult for organizations to protect their data, as technology continues to rapidly evolve and change the working practices of organizations and people. This is where managed SIEM services come into play.
Increase ROI
Results can be achieved at a fraction of the cost of hiring an experienced full-time security team. Internal labour, recruitment, hardware, management, and support costs all quickly add up but do not necessarily guarantee faster investigation and resolution of cyber incidents.
Case study
Read about how LRQA Nettitude provided urgent incident response services to a multinational online retailer who realised their IT network had been compromised.
Speak to us about our Managed SIEM solution…

Our close partnership with LogRythm
We have been named as LogRhythm’s managed security service partner (MSSP) of the year three times. We enjoy close technical and commercial relationships with LogRhythm, a Gartner leader in SIEM technology.

A Microsoft Solutions Partner for Security
We are a Microsoft Solutions Partner for Security. This designation recognises LRQA Nettitude’s deep understanding of Microsoft technologies and showcases a proven track record of successfully implementing security solutions.
Become ransomware resilient
• 40% of organizations have experienced significant downtime because of ransomware attacks, and 36% have reported a loss in revenue.
• The average ransom paid by mid-sized organizations in 2021 was $170,000. However, the average bill for fully rectifying a ransomware attack was $1.8 million.
Ransomware attacks can very quickly put your organization in a very threatening situation, resulting in operational paralysis, financial penalties, and long-term reputational damage.
Get in touch to become ransomware resilient…
Get a ransomware resilience assessment
Our skilled experts have extensive experience of dealing with complex cyber investigations and ransomware attacks. They are supported by cutting-edge technologies that help you to reduce your exposure to ransomware and increase your ability to recover quickly in seven steps.
Access leading technologies
We enjoy close technical and commercial relationships with leading providers for active defence, endpoint detection and response (EDR), and vulnerability scanning. All key tools to help protect you from ransomware threats.
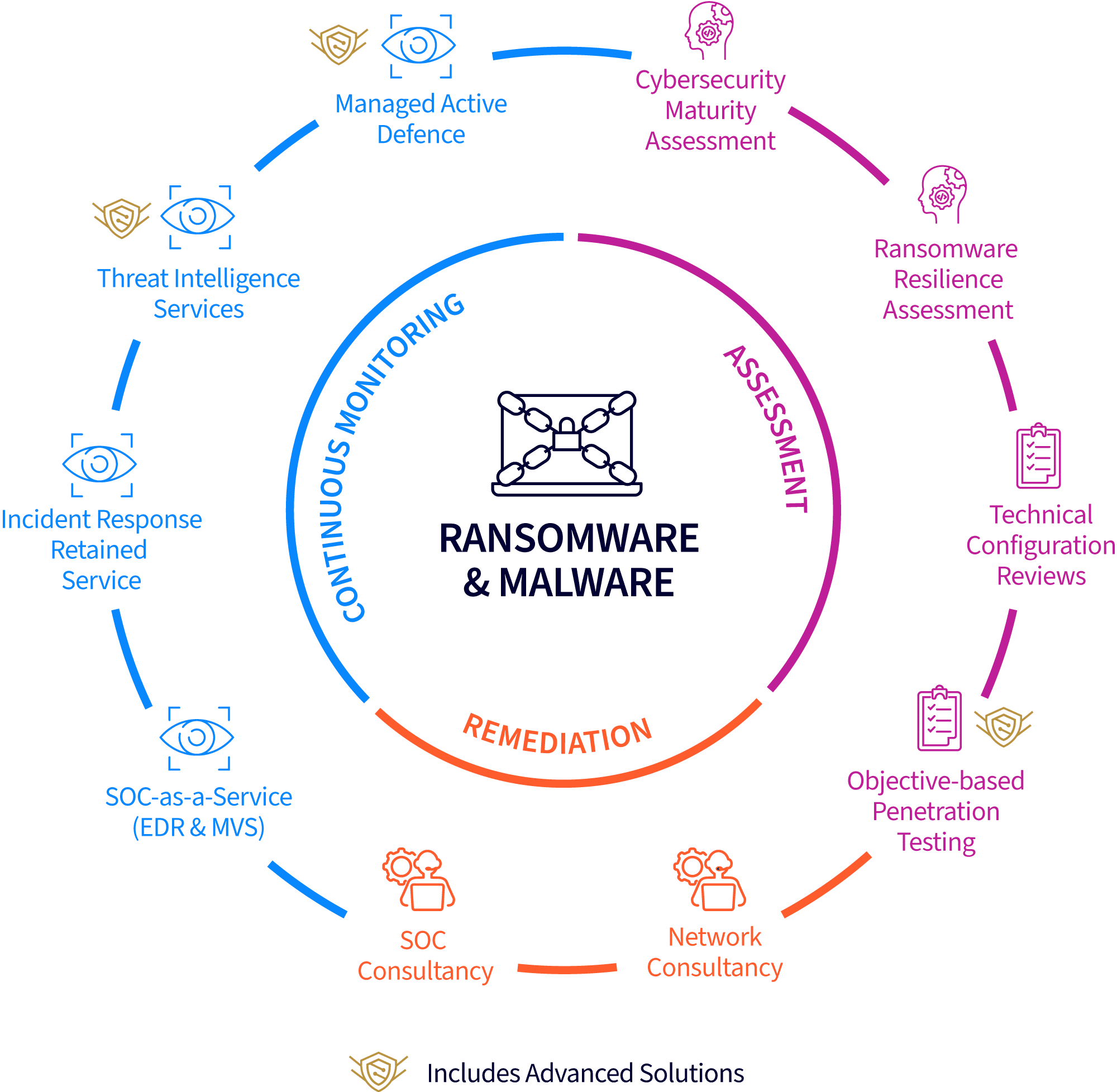
Get in touch to become ransomware resilient…
Select an option below…
BREACHES HAPPEN.
What matters is how you respond to them
LRQA Nettitude have been preparing organizations for, responding to, and managing cyber incidents across three continents for over 20 years. Are you prepared for a cyber incident?
Get immediate assistance
If you know, or even just suspect you are experiencing a cyber incident then time is of the essence.
Get immediate assistance…
Incident Response
Our incident response management helps reduce the impact of a cyber-breach by immediately sending assistance to your organization.
We only work with and deploy leading incident response technologies including:



Why is a rapid and thorough response essential?
- Preventing the spread will reduce the cost of recovery
- It will reduce the recovery time required
- Increase the likelihood that more parts of your business will be able to function as normal during remediation
“LRQA Nettitude’s early advice prevented a full deployment of ransomware malware across our entire IT network. Their timely response and investigation enabled the business to reduce the impact of the breach and continue operations.”
We are the only organization in the world with a full suite of CREST accreditations
Our Incident Response Team includes:
- CREST Registered Intrusion Analysts
- CREST Certified Network Intrusion Analysts
- CREST Certified Malware Reverse Engineers
Prepare your incident response plan
• Organizations who are prepared with an incident response team that stress test their cyber plans save $2.4 million versus those who do not
We only work with and deploy leading incident response technologies including:



Companies who prepare better, perform better.
Knowing how to detect a cybersecurity breach and having a response plan in place are essential fundamentals for any organization. This means engaging with the right people, with the right skills, who have access to the right tools on hand 24/7/365.
We can drill and regularly test your internal teams to ensure they know the procedures to follow to contain and remediate a cyber incident.
“We are now in a much stronger position to detect and respond to attacks. Sentinel is fully deployed and monitoring the IT estate, and the whole business is now taking a much more mature approach to cybersecurity. The executive team now have the assurance that the business is prepared for further attacks and will be able to respond appropriately.”
Book an incident response demo…
Providing value for our global clients
A programme of this magnitude is complex and difficult to administer in terms of staff turnover, training, and sourcing/integrating the right tools. This is where LRQA Nettitude provides value for our global clients.
Introducing NCIRT
Our incident response team are highly trained, experienced, and committed to helping you at every stage of the incident response lifecycle. From preparation and eradication, through to remediation and lessons learnt we are available 24/7/365.
Case study
Read about how LRQA Nettitude provided urgent incident response services to a multinational online retailer who realised their IT network had been compromised.
Managed SIEM solution
• Only 28% of organizations integrate their security controls into a security information and event management (SIEM)/security orchestration, automation, and response (SOAR) platform to orchestrate their response to an attack.
We only work with and deploy leading incident response technologies including:




Immediate results
It is increasingly difficult for organizations to protect their data, as technology continues to rapidly evolve and change the working practices of organizations and people. This is where managed SIEM services come into play.
Increase ROI
Results can be achieved at a fraction of the cost of hiring an experienced full-time security team. Internal labour, recruitment, hardware, management, and support costs all quickly add up but do not necessarily guarantee faster investigation and resolution of cyber incidents.
Case study
Read about how LRQA Nettitude provided urgent incident response services to a multinational online retailer who realised their IT network had been compromised.
Speak to us about our Managed SIEM solution…
Access leading technologies

Our close partnership with LogRythm
We have been named as LogRhythm’s managed security service partner (MSSP) of the year three times.
We enjoy close technical and commercial relationships with LogRhythm, a Gartner leader in SIEM technology.

A Microsoft Solutions Partner for Security
We are a Microsoft Solutions Partner for Security. This designation recognises LRQA Nettitude’s deep understanding of Microsoft technologies and showcases a proven track record of successfully implementing security solutions.
Become ransomware resilient
• The average ransom paid by mid-sized organizations in 2021 was $170,000. However, the average bill for fully rectifying a ransomware attack was $1.8 million.
Ransomware attacks can very quickly put your organization in a very threatening situation, resulting in operational paralysis, financial penalties, and long-term reputational damage.
Get in touch to become ransomware resilient…
Our skilled experts have extensive experience of dealing with complex cyber investigations and ransomware attacks. They are supported by cutting-edge technologies that help you to reduce your exposure to ransomware and increase your ability to recover quickly in seven steps.
Access leading technologies
We enjoy close technical and commercial relationships with leading providers for active defence, endpoint detection and response (EDR), and vulnerability scanning. All key tools to help protect you from ransomware threats.
Get in touch to become ransomware resilient…
The world leader in CREST accreditations

We are proud to be the only organization in the world with a full suite of CREST (The Council of Registered Ethical Security Testers) accreditations.
Select an option below…





